Introduction to Essential Data Governance and Management System(EDGS)

Introduction to Essential Data Governance and Management System(EDGS)
2022/12/30
I. Background
Along with organizations face the industrial, social and economic level of Digital Transformation trend brought by the development of emerging technology or the occurrences of disasters or emergencies(such as COVID-19), and so on. Inducing the increasing demand for transformation of digital governance and management. Including the board of directors and the top managements’ decision making, supervision to internal audit, internal control etc. It is necessary to establish and implement the digitized management measure of content or process step by step. Strengthening the reality, integrity and full disclosure of data, in order to improve the efficiency of organizational decision making, execution, supervision and management.
Although implementing the digitization process, brings convenience and efficacy to the organization, accompanied by risks. Digital data has characters of being easy to modify and spread. This often results in difficulty for the original version owner in proving the originator’s identity and then impacts rights protect. Additionally, when cooperating with others, the organizations may provide essential digital data to others, or receive others’ essential digital data. When data breaches or controversies occur, it is required to have measures assisting in the identification or prove the origin of the data. In order to delineate the responsibilities and enhance mutual trust.
Essential Data Governance and Management System(hereinafter referred to as, EDGS) is a management model which is to be introduced at the discretion of each organization. Looking forward to improve the degree of the ability in organizations’ digital and governance level progressively. Starting to improve the protected process of the digital data in the first place, reinforcing the long-term preservation of validity of the essential digital data. In order to guarantee the evidence capacity and reinforce the probative value by the time litigations has been instituted or the related competent authority investigates.
II. Setting Objectives
The purpose of EDGS is to help organizations consolidate with existing internal auditing, internal control or other management process and then implement tweaks that establish an organizations’ essential data governance and management system that meets the requirements of EDGS. In order to attain the following benefits(as shown in Figure 1 below):
a. Improve the digitalization level of governance and management in internal control, internal auditing or surveillance.
b. Improve organizations’ cooperation, trust and the chance of digital transformation.
c. Reinforce organizations to identify and manage the self-generated, provided or received external digital data.
d. Reinforce organizations’ validity of evidence presented in litigation or the inspection certification of competent authority.
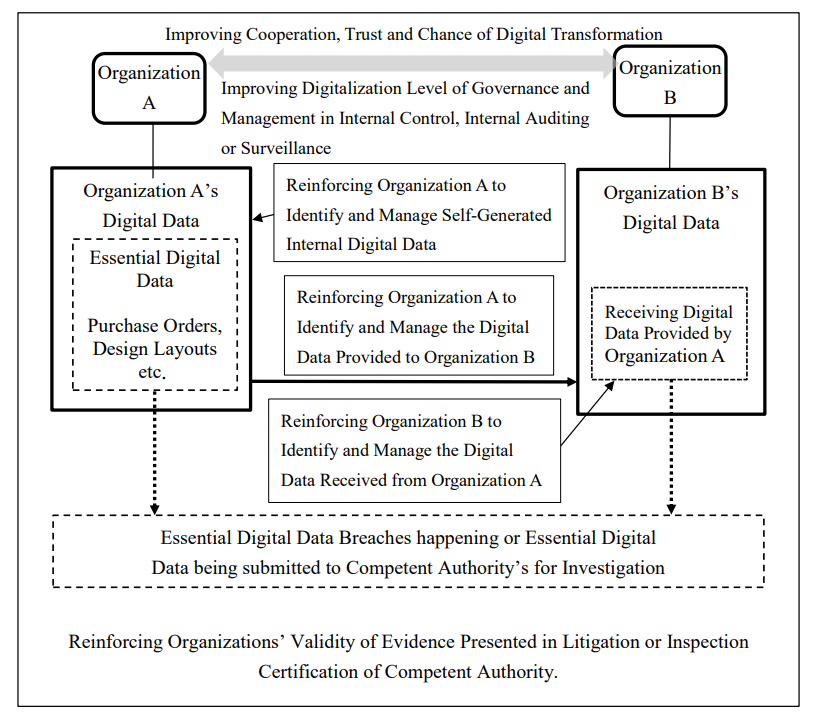 Figure 1: Setting Objectives of EDGS
Figure 1: Setting Objectives of EDGS
III. Scope of Application
EDGS is designed to be applicable to all organizations, regardless of their type, size, and the products or services they provide. In addition, the requirement of EDGS are centered on the organizations’ essential data governance and management system process (as shown in Figure 2 below). The so-called organizations’ essential data governance and management system process refers to from the digital data process of generation, protection and maintenance to the digital evidence preservation information process of acquisition, maintenance and verification by setting management objectives in accordance with the management policies established by the organization.
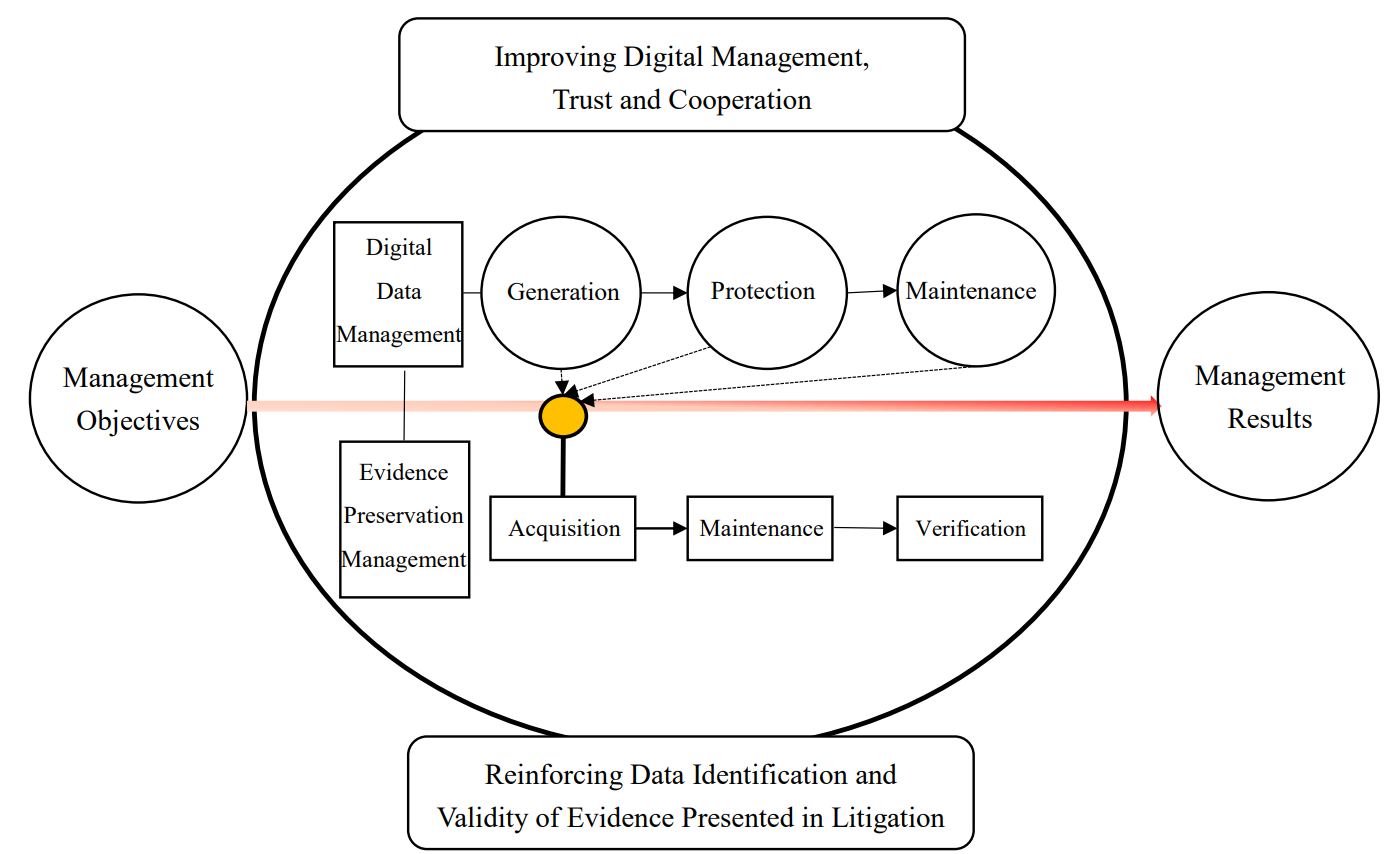 Figure 2: The Conceptual Flow Chart for the Organizations’ Essential Digital Data Governance and Management System Process
Figure 2: The Conceptual Flow Chart for the Organizations’ Essential Digital Data Governance and Management System Process
IV. Process of Application
EDGS encourages organizations to link and reinforce the existing “process management” approach and “PDCA management” cycle(as shown in Figure 3 below) in developing, implementing and improving their essential data governance and management system.
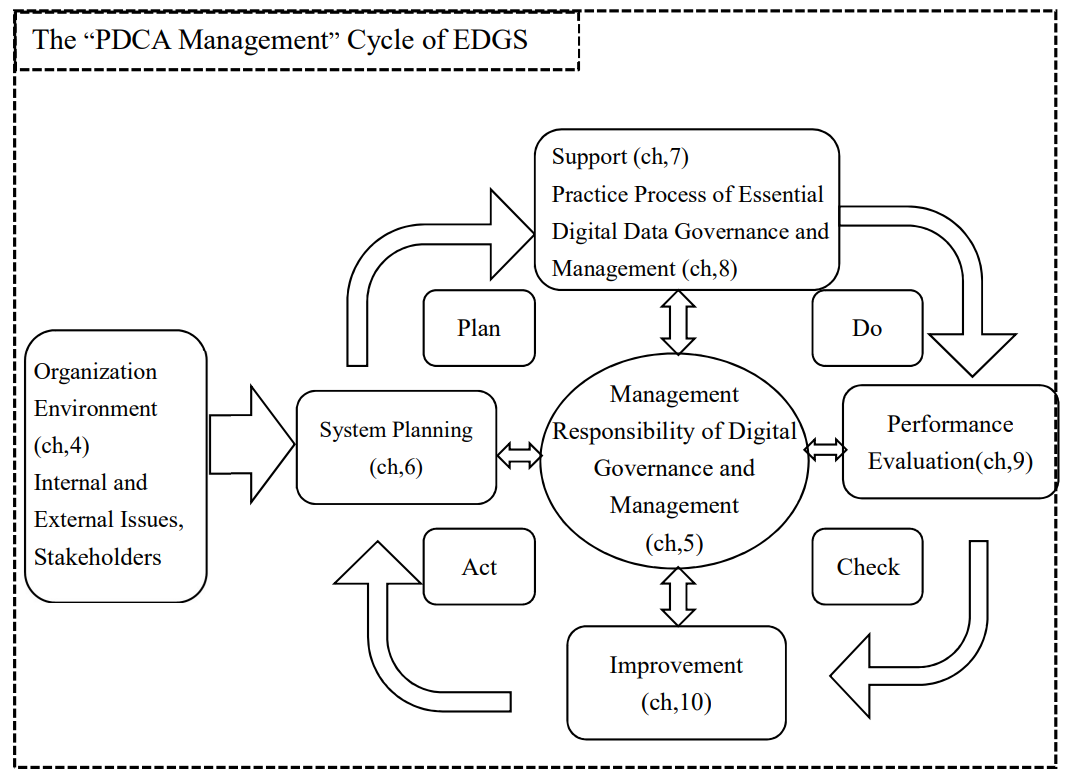 Figure 3: The “PDCA management” Cycle of EDGS
Figure 3: The “PDCA management” Cycle of EDGS
V. Table of Contents
Chapters 0 to 4 of EDGS are the description of the system structure, scope of application, definition of terms and consideration factors; Chapters 5 to 10 are important management items.
| 0. Introduction 0.1. General Description 0.2. Target 0.3. Process Management 0.4. Management Cycle 0.5. Setting Objectives 0.6. Compatibility with other management systems |
| 1. Scope of Application |
| 2. Version Marking |
| 3. Definition of Terms 3.1 Organization 3.2 Digital record 3.3 Identification Technology 3.4 Metadata 3.5 Hash Function 3.6 Hash Value 3.7 Time-Stamp |
| 4. Organization Environment 4.1 Internal and External Issues 4.2 Stakeholders |
| 5. Management Responsibility of Digital Governance and Management 5.1 Management Commitment 5.2 Management Policy 5.3 Management Objective Planning 5.4 Management Accountability and Communication |
| 6. System Planning 6.1 Basic Requirements 6.2 Response to Risks and Opportunities 6.3 Change Planning |
| 7. Support 7.1 Resources 7.2 Personnel 7.3 Equipment or System Environment 7.4 Communication Channels |
| 8. Practice Process of Essential Digital Data Governance and Management 8.1 Generation, Maintenance and Protection of Digital Data 8.2 Acquisition, Maintenance and Verification of Digital Evidence Preservation Information |
| 9 Performance Evaluation 9.1 Basic Requirements 9.2 Data Analysis 9.3 Internal Audit 9.4 Management Review |
| 10 Improvement |
For the full text of the EDGS(Chinese Version), please refer to:
https://stli.iii.org.tw/publish-detail.aspx?d=7198&no=58
Chen Yi-Chih, Chen Hung-Chih 2 I. Foreword Intellectual Property (IP) Management is a subject of recent focus in Taiwan . More than 1 million patents have been filed in Taiwan and each year, Taiwan dedicates NT $80 3 trillion in research and development. The estimated cost for IP prosecution, maintenance, litigation, conciliation, compensation and authorization amounts to NT $200 trillion (U.S.$6.5 trillion) 4. Even though many enterprises have gradually recognized the importance of intellectual property, the situation has not significantly improved based on the statistics stated above. Observation shows that only few enterprises in Taiwan have taken active steps to manage their IP and it was only after facing infringement lawsuits and tremendous amount of loyalty payments, most companies started to realize the important of IP management. Two main causes are believed to have negative impact on the lacking and ineffectiveness of most Taiwanese enterprises' IP management: Taiwanese enterprises have not taken proactive measures to handle IP management issues and IP management is only viewed as a mechanism to prevent IP infringement. Taiwanese enterprises have not sought ways to proactively and strategically use their intellectual property as a tool to yield profit. Due to limited professional knowledge and resources, Taiwanese enterprises do not know how to manage and exploit IP generated within their companies . Therefore, it is critical to assist these enterprises to develop and implement an effective IP management strategy under which the full potential of their IP can be utilized and the maximum value of the enterprises' IP can be realized. The Intellectual Property Office of the Ministry of Economic Affairs recognized the importance of governmental role to address this issue. Since 2003, it has collaborated with the Institute of Information Industry to work on a project for developing a standardized IP management system. In 2005, the project was handed over to the Industrial Development Bureau which then carried on the development and promotion of the Taiwanese Intellectual Property Management System (TIPS). Taiwanese enterprises 5 are able to use TIPS as a basis to establish their own comprehensive IP management systems. Based on our experiences in promoting TIPS and the feedbacks from those enterprises which have followed the TIPS's guidance to establish their IP management systems, we are pleased to find that TIPS is capable of assisting enterprises to develop a comprehensive IP management system. The system no only meets an enterprise's operational needs but also can be continuously improved owing to its adoption of the PDCA management cycle 6. II. The Introduction of TIPS A. The Origin and Overview of TIPS On December 9, 2004, The Ministry of Economics, in recognition of the needs to assist Taiwanese enterprises to better manage and more fully utilize their intellectual property, organized a “Taiwanese IP Management Standardization and Promotion Summit”. In order to establish a consensus on IP management among Taiwanese enterprises and to encourage the enterprises to implement an internal IP management system, the Taiwanese government positioned TIPS as an industry standard. In 2006, The Industrial Development Bureau (IDB) of the Ministry of Economic Affairs (MEA) established a TIPS promotion program and revised the 2004 draft of the Intellectual Property Management System Standard to become the Taiwan Intellectual Property Management System (TIPS). The industrial experts' opinions and comments were gathered and used to amend the draft, TIPS was then formally announced 7 on March 23, 2007 and consequently promoted. In hopes to protect Taiwanese enterprises and to improve their market competitiveness, IDB initiated extensive promotion program, encouraging Taiwanese enterprises and organizations to establish a convenient, efficient, and low-cost IP management system by following the TIPS's guidance The main characteristic of TIPS is the incorporation of the PDCA (Plan-Do-Check-Action) model from the ISO 9001:2000 Quality Management System. By adopting this model, not only the challenges of IP management can be resolved, but the whole system can also be continuously improved. Since TIPS shares the ISO's characteristics of being credible, comprehensive, and easily adaptable, TIPS and be easily integrated into the ISO standards within an enterprise such that the conflicts between these two systems will be minimized and it will only require minimum organizational structural changes and implementation costs. If an enterprise has already implemented ISO, implementing TIPS becomes more easily and efficient. In addition, TIPS emphasizes the concepts of using “process-oriented approach” and “systematic management” 8. Enterprises can merge their existing infrastructures and TIPS to establish a convenient, effective and efficient IP management system to reduce losses caused by IP infringement. Enterprises may also strengthen their market competitiveness and increase profits through royalty income. TIPS includes nine chapters. The first four chapters cover Summary, which describes the background of TIPS; Scope of Application and Terminologies. Clause 0.3.1 9 of TIPS states that the purpose of TIPS is to promote the utilization of IP management as one of the means to maximize an enterprise's profits. Rather than an individual or a specific department, protecting IP assets is the responsibility of all employees within the enterprises. In addition, the establishment of an IP management system is essential regardless of the scale, product or service provided by an enterprise. Clause 1.2 of TIPS clearly provides that TIPS is applicable to all enterprises, despite their types, scales, products and services provided. Therefore, TIPS is not designed solely for large enterprises. It can be applied to all kinds of organizations which include but not limit to a company, a specific department/division within a company, a laboratory or a project team. B. The Foundation of TIPS Before establishing TIPS, the government recognized that an enormous amount of resources is required to establish an IP management system. Therefore, the ISO9001:2000 quality management framework was adopted and TIPS was developed based upon the ISO's management principles. By incorporating IP managing strategies into an enterprise's operation goals and internal activities, the IP management system is no longer just a risk management system but a system that is closely aligning to the overall operations of an enterprise. Since it was found that many domestic companies implemented ISO9001:2000 Quality Management System solely for compliance purposes, people are skeptical about its effectiveness. In fact, if one understands the rigorous formulation processes behind the quality management system and its principles, one would recognize that an enterprise's IP management system can be significantly improved by adopting the management characteristics of ISO Quality Management System. The main characteristics shared between TIPS and ISO are outlined as follows: The effectiveness of an IP management system can be evaluated through clear policies and goals Chapter 5 of ISO 9001 : 2000 discusses Management's Responsibility. It states that top management should establish an enterprise's mission, vision, policies and goals, otherwise known as Visionary Leadership. An enterprise should consider its stakeholder's needs, understand the gap between its current status and the ideal state when setting its mission, vision, policies and goals. It should also decide its operational goals by considering available resources and the external environment. Traditional way of IP management only focuses on the operational and managerial processes. Strategic issues such as strategic planning and mission/vision planning are often forgotten, which often leads to a disconnection between strategy and actual operations. The concept of setting clear policies and goals used in ISO Quality Management shall be adopted to manage IP. That is to say, clear policies and objectives should be defined by the top management followed by detailed processes and steps required to realize the goals. Clear operational processes and responsibility help to achieve IP management goals ISO9001:2000 states that quality issues are caused by process, not product and process issues are caused by management since processes are carried out by people. Therefore, all personnel who is involved in carrying out the processes (in other word, all the employees within an organization) shall have the responsibility to improve quality. This concept applies to IP management as well. It is an incorrect general belief that IP management is merely for damage control or risk prevention. It is also an incorrect belief that an IP management is the sole responsibility of the legal department that other departments have no roles to play in enhancing the added-value of IP. For enterprises intending to utilize IP to enhance its competitiveness, some suggestions as listed below should be taken into account when planning their IP strategies: Set IP management as one of the company's operational goals. Organize a team to implement the IP strategy and to determine the processes required to achieve the IP goals. Clearly identify roles and responsibilities for personnel involved in all levels of IP management. Identify tasks required to be documented. Ensure the employees understand the linkage between their assigned tasks and the corresponding organizational goals. Through careful considerations of planning the organizational goals, processes and the expected outputs derived thereupon, enterprises can determine whether the processes so planned are necessary, appropriate, and effective . Consequently, minimizing the resources required to be invested into IP management. Monitoring, evaluation, and corrective actions can help to ensure the effectiveness of an organization's IP management processes Clause 8.2.1 of ISO9001:2000, “customer satisfaction”, emphasizes that customers own the right to evaluate. In the case of IP management, customers are basically the enterprise itself, therefore the performance is evaluated based on whether the set organizational goals can be achieved. It has been observed that many companies implemented the ISO Standards purely for the purpose of obtaining ISO's certification and do not consider whether the processes implemented are, in the practical sense, effective or efficient. Under this circumstance, the enterprises would not gain any actual benefits, despite that the requirements of ISO standards are met. The goal of process management is to improve the process efficiency, effectiveness and adaptability. Clause 8.2.3 of the ISO9001:2000 discusses Monitoring and Measurement of Process and Clause 8.2.4 talks about Monitoring and Measurement of Product. They state that an organization should establish a mechanism to monitor, evaluate, and understand the organization's internal and external customers' needs. This mechanism can also help to determine whether the organization can meet or exceed the expectation of its customers (in terms of processes, products, and/or services), which is also a critical element in establishing a systematic IP management system. If the result of evaluation does not meet expectation, there is a problem. In order to prevent the problem from reoccurring, prevention is the best. The concept of prevention is to design measures to avoid the occurrence of hidden problems. Unexpected problems are inevitable to occur even if preventive measures have been taken. We should analyze the impact of the problems occurred and propose counter measures to minimize their impact. The efficiency of IP Management relies on continuous improvement There are always opportunities to improve any process. Clause 8 of the ISO9001:2000 discusses Measurement, Analysis and Improvement which includes continuous improvement processes. Clause 8.2 Monitoring and Measurement, Clause 8.3 Control of Nonconformity, and Clause 8.4 Analysis of Data discuss the issues surrounding monitoring, measurement, analysis and control of nonconformity. Clause 8.5 discusses Improvement, which covers action taken to address the causes of identified issues. There are many issues that may be identified after analysis which cannot be resolved at once. Clause 5.1 of ISO 9001:2000 Management Commitment requests that the top management team be responsible for setting policy and goals, and providing resources needed to achieve the goals. By introducing ISO9001:2000 measurement, analysis, and improvement methodologies into the IP management system, it is believed that enterprises can thus effectively manage their IP and achieve a win-win scenario with their customers. C. The expected benefits of Implementing TIPS Since TIPS shares the above mentioned characteristics of the ISO Quality Management System, it not only can reduce the risks of infringing the IP rights of the others, but also can assist an organization to achieve its operational goals provided that the organization has designed relevant processes pursuant to the requirements of TIPS and has thoroughly implemented the designed processes. Using TIPS's external evaluation mechanism 10, enterprises implementing with TIPS can prove to their customers and external stakeholders that they have the capability to manage and maintain their IP. If an enterprise follows TIPS to establish its IP management system, its expected benefits include the followings: Enhancing market competiveness and increasing the added-value of an organization An IP management system that is designed to meet the specific needs of an organization shall play a significant role in achieving the organization's operational goals. Take a fitness equipment or an automobile parts manufacturer as an example, if the manufacturer owns the IP rights (ex: new design patent or trademark) embodied within the products, it is expected that the manufacturer can profit more than a purely OEM company which does not own its own brand. This is because the IP rights embodied within the products could provide significant added-value beyond what an OEM company can offer. Increasing customer's ordering intent The guidelines of TIPS also serve as the requirements for certification purpose. A government certified IP management system will ease concerns over trade secret protection and thereby promote cooperation and trusting relationships between the suppliers and the buyers and between research collaborations which consequently would foster better research results and potentially more purchasing orders. Minimizing resource wasting and actively creating profits Most small and medium enterprises in Taiwan do not have adequate labor and financial resources to develop a comprehensive IP management system. It is the hope of the government that a simple, effective, and low-cost IP management system can be established which tailors to the specific needs of every enterprise by adopting the TIPS framework. Once enterprises are capable of systematically manage their IP, it is expected that the IP generated and their exploitation can really match the enterprises' requirements and expectations, so that no resource is wasted to produce unwantable IP. The enterprises may further increase their profits by licensing or assigning their IP rights. Fostering an organizational culture that values the importance of intellectual property and the ability to continuous improve Establishing IP management policies, coupled with ongoing IP management seminars and education and training programs for new employee would enhance the awareness of the importance of IP management to the organization among the employees. The employees may further change their attitudes from passively complying with the policies to actively participate the system such as paying particular attention to potential IP risks and offer suggestions for process improvement. One company which implemented TIPS commented that the regular and ad hoc audits requirement and the necessity of assigning roles and responsibilities as required by TIPS assist it to identify problems concerning management issues. Corrective and preventive actions can be rapidly taken to address the problems identified, allocate the liabilities and improve the whole system. As a consequence, the IP management system can be effectively carried out to ensure that the planned objectives are met. It was found that most companies do not have internal audit and continual improvement programs to detect the hidden problems concerning management. Enhancing risk management and the capability to respond Currently, the fundamental and most important goal for an enterprise's IP management is to reduce the risks of infringement. Enterprises which have implemented TIPS found that TIPS is capable of enhancing data sharing across the departments which allows the IP department to detect potential risks at the earliest time. Further, the establishment of risk management mechanism and processes in response to infringement allegations as required by TIPS helps to institutionalize an enterprise's management system in handing legal risks. III. A holistic approach to IP management The Taiwanese government hopes that enterprises can systematically manage their IP through the implementation of TIPS. In other words, following TIPS's guidance, the Taiwanese enterprises should establish an IP management system that incorporates the usage of the PDCA management cycle (Plan-Do-Check-Action) and process management approach and such system must be built by taking into account the enterprise's business operation strategies and objectives. Enterprises should have clear processes and related rules for handling all IP related issues. For example, prior to filing a patent application, there should be a plan for the ways to acquire the targeted IP and prior art research shall be conducted. Based on the search results, enterprises can then decide whether they would like to internally develop the targeted IP or to seek licensing opportunities. Effective IP management processes shall be able to answer the following questions: Whether records are stored property? Who should conduct the audit? Whether the current system meets the IP management policy or goals? What are the roles and responsibilities? The following section aims to explain how Taiwanese enterprises can establish or modify their current IP management system to achieve its full potential: A. Roles and Responsibilities for Implementation All employees within an organization shall participate in order to realize the most benefits out of the IP management system. Leadership responsibilities, roles and responsibilities allocation, training and education programs and the subsequent auditing processes on the performance of operation shall be clearly defined and planned. Establishing a successful IP management system shall not be the sole responsibility of the legal department. During the implementation stage, the following personnel should participate and complete the related tasks: Executive management team (Management executives, ex. CEO, President, COO) a. Establish IP management policy and goals; b. Communicate the importance of compliance to the IP management policy; c. Evaluate and review the effectiveness of the IP management system; and d. Ensure the readiness of the resources available for establishing the IP management system. IP Management System Representatives (Managers who have decision-making authority, ex. EVP, VP) a. Ensure that the required processes for the IP management system are established, implemented, and maintained; b. Report to the executive management team on the performance and improvement needs for the existing system; and c. Ensure employees understand the IP management policy and goals. Department Representatives (All department representatives) a. Execute tasks assigned by the IP management system representatives; b. Execute action items reached by the steering committee meetings; c. Ensure the achievement of IP management goals, and d. Responsible for the Maintaining and improving the IP management system. B. Steps of Implementation Plan Establishing a systematic IP management system requires the participation of all employees and it requires reengineering of the existing processes. It is not an easy task to be established and planned solely by the legal department. All other departments within an enterprise shall participate and offer their suggestions. The followings are the recommended stages for implementing an IP management system: Stage Tasks Description Responsibility Remark 1. Preparation 1). Review of current status Understand resources available and the status of operation Data collection; define roles and responsibilities 2). Establish implementation team Identify team members and team leader Confirm organizational structure for implementation 3). Set goals and establish all management programs Evaluate current situation to formulate IP management policy, and define measurable goals. Processes planning shall be made by taking into account the management responsibility, resource management, product development, and performance analysis and improvement. This helps to identify the position of a process within the overall IP management system and its inter-relationships between the processes themselves. Provide evaluation report; organize IP management deployment document Documentation: IP Management Manual à Procedures à Guidelines à Records 2. Training and Education & System Integration 4). Relevant training and education Understand the direction, method, and spirit of standardization. Participated by the implementation team and management representatives. 5).Drafting documentation Decide documentation framework, format, table of contents, numbering principles, and appoint editors and the completion date. Management team assigns tasks 6). Establishing documentation Drafting and revising procedural documentation Internal discussion and review IP management principles (refer to prior text) Define the scope and content of standard format. Appoint editors and the completion date. Establish standard format as an example before documenting Prepared IP management manual to aid employees and customers to understand the organization's IP management system Implementation team and management team 3.Implementation 7). Provide training & education specifically for the internal audit personnel Explain the purpose of auditing and execution details Participated by Internal audit committee Prepare checklist for auditing to be used by auditing personnel 8). Conduct system implementation and internal audits Execute documentation processes for the management system and conduct internal audits and review the performance Implementation, review, correction and prevention. Participated by all employees 9). Conduct overall examination of the intellectual property management system Implement IP management system Participated by all members of the implementation team C. Implementation Chapter five through chapter eight of TIPS define the core of the guidelines which cover the basic requirements of IP management requirements; top management's responsibilities; resource management; the acquisition, protection, maintenance and exploitation of IP, as well as performance evaluation and improvement. To facilitate Taiwanese enterprises' understanding of TIPS and how to use it to establish a comprehensive IP Management system, we provide the following main steps of establishing an IP management system based on the TIPS's requirements: Define the company's IP management goals Enterprises that would like to establish an IP Management system have to understand their unique features and future operation strategies to evaluate the needs for managing their IP. Clauses 4.1, 5.2, and 5.3.1 of TIPS stipulate that the management team has the responsibility to set clear IP management policy and goals. For example, one policy can be to increase R&D efficiency and the goal can be to reduce the product development cycle by 10%. Defining appropriate IP Management policies can help to establish a IP management system that meets an enterprise's practical needs. It can also be used as basic principles for formulating IP strategies and subsequently the implementation processes of IP management system. The management team should utilize intranet or bulletin boards to inform its employees of the organization's IP management policies, goals, and relevant responsibilities assigned to each department. This will help employees to understand their roles and responsibilities and the importance of their participation in achieving the organization's goals. Develop required processes for achieving enterprise's IP management goals The ultimate purpose of establishing an IP management system is to maximize profits and to minimize losses. To ensure successful acquisition of targeted IP, companies should plan and develop processes and operating procedures based on their needs and business development strategies. During this stage, companies should focus on the followings in order to meet TIPS's requirements: Understand statutory and regulatory requirements concerning IP The management target of TIPS is intellectual property, which includes trademark, patent, copyright, trade secrets and etc. Different IP acquisition approaches apply to different IP targets. Complying with Clause 7.1, companies must firstly understand all the statutory and regulatory requirements before a plan is made for the acquisition of targeted IP. For example, according to the relevant legislations in Taiwan, once a work is created, the authors obtain the copyright in the work. However, the right to patent or trademark can only be acquired through registration. Evaluate options for acquiring the targeted IP Enterprises shall evaluate different options (i.e. self-development, purchase or outsourcing) for acquiring their targeted IP by taking into account of their business operation objectives and the characteristics of their products as the methods of acquiring IP will influence the subsequent processes concerning the protection, maintenance and exploitation of the acquired IP. Clause 7.2 of TIPS requires enterprises to implement processes regarding to the evaluation of the options for acquiring the targeted IP. Clause 7.3.5 further requires enterprises to set up an assessment procedure for every IP application and suggests to incorporate an invention incentive program. Define roles and responsibilities After completing the feasibility study concerning various options to acquire the targeted IP, enterprises have to decide whether to establish an IP management specialized department (ex. legal or IP department) and to define clear roles and responsibilities based on the company's scale and resource available. Companies should pay particular attention on preparation work, such as conducting patent or trademark prior art search, to avoid wasting of resources and voided applications. If enterprises outsource IP management related activities to external bodies, Clause 7.4.1 of TIPS requires them to have a clear knowledge of the service quality provided by the outsourcing bodies and to establish a controlling mechanism over the outsourcing activities (ex. evaluation → outsourcing → contract → periodic evaluation…etc.). Special attention has to be paid to the contractual terms concerning obligations and ownership of IP. Determine Resources Required Enterprises that would like to establish an IP management system not only have to ensure that they have enough resources, but also need to ensure that the resources can be utilized in an effective way. The management team, in accordance of the requirements for Clauses 5.4.2 a nd 6.1 of TIPS, should provide resources (including labor and equipment) required for the implementation of the IP management system. Examples include the continual recruitment of manpower and the purchasing of computer software and hardware equipments and etc. As far as labor is concerned, enterprises, in accordance with Clause 6.2.1 , have to ensure that their employees have adequate abilities to assume their responsibility. Clause 6.2.1 states that companies should provide basic IP education and training to equip the employees with necessary knowledge. Pursuant to Clause 6.2.3, enterprises should provide their patent engineers and legal staff with advanced training, such as intellectual property litigation and arbitration, intellectual property licensing and contracts, techniques for patent design around, IP valuation and so on. In summary, enterprises should enhance the employees' (both new and existing employees) awareness of IP, the importance of complying with statutory requirements and the enterprises' internal IP policies and goals through education and training. Establish an IP Management System After determining the resources required, enterprises need to establish a basic system to manage their IP. The system shall include a documentation control system, an audit program, an internal communication channel and so on. We provide a summary explaining the details of each program required to establish a basic IP management system: Basic IP Management System (1) Documentation Control System: Enterprises should establish a systematic documentation control system based on their IP management policies and goals, such as document control procedures, internal audit process and etc. Among those, the most important one is an IP management manual. Clause 4.3 of TIPS requires the enterprises to state all the following items in their IP management manual: IP management policies and goals; roles and responsibilities; processes and procedures; and flow charts or grid charts to explain the interrelationships between the processes and procedures. Further, Clause 4.4 also states that all documents, no matter whether they are internally generated or externally acquired (ex. court notice, invitation to tender, official documents) should be properly managed. The source, level of confidence, method of management should be clearly labeled for future purposes. (2) Audit Program: Clause 5.4.2 states that top management has to be responsible or otherwise shall designate a management representative (the most senior staff that is responsible for intellectual property matters, such as vice president or director of IP management department) to manage a company's IP related issues. The top management team is also in charge of establishing a management review meeting, and setting agenda for each meeting such as discussing or revising the IP management policies and goals. Through management review meeting, pursuant to Clause 5.5, management representative must confirm that the set IP goals are met or if not, whether to revise the original policies or goals. All departments or responsible personnel (ex. legal, IP, general administration, accounting, human resource) shall participate the management review meeting. (3) Confidentiality Control Program: Enterprises in accordance with Clauses 4.4.1 a nd 7.4.4, should enhance feasible safety controls to protect their IP, such as setting document confidential criteria, physical access control, and control over replication of confidential documentation to limit exposure of important data. Supplemental IP Management System In addition to the above mentioned programs, supplemental IP management programs are required to assist in establishing an effective IP management system. They are outlined as follows: (1) Outsourcing Program: Due to cost or resource concerns, enterprises may outsource its R&D or IP prosecution activities to external professional agencies. Clauses 4.1 and 7.4.1 of TIPS require that the contracts entered into must clearly identify the ownership of IP involved and include a term of confidentiality obligation. This is to ensure that the outsourcing activities can be properly monitored and to prevent the leakage of important data. (2) Contract Review and Human Resource Management Programs: In order to prevent and avoid intellectual property infringement, in accordance with Clause 7.4.6 , enterprises should review all contractual terms of their contracts. As far as human resource management is concerned, in accordance with Clause 7.4.3, enterprises shall require new employees to sign an employment contract . Such contract shall include a term of confidentiality obligation and a non-competing clause may be included if necessary. (3) Internal Consulting and Communication Channel: During the period of establishing an IP management system, enterprises in accordance with Clause 5.5.2 must request relevant departments (ex. legal, sales, finance and accounting) to provide useful information concerning IP management. According to Clause 5.4.3, enterprises must establish communication channels (ex. dedicated mailbox, email) which is used to understand the feelings and to know the difficulties faced by the employees as it is inevitable to face challenges when a new system is being implemented, consistent communication and coordination is the only way to overcome these challenges. Ensure that Auditing and Preventive and Corrective Measures have been Taken Pursuant to Clauses 8.1 and 8.2, enterprises with IP management systems need to establish internal audit plans (including audit frequency, time, or method) to ensure that their IP management policies or goals are being met. Enterprises should ensure that their internal auditors are qualified i.e. have obtained the relevant professional certification, before conducting the internal audits. If nonconformities have been found through internal audits, corrective or preventive measures should be taken pursuant to Clauses 8.4.2 a nd 8.4.3. For instance, if the result of internal audit reveals that the R&D staff failed to keep their R&D records in accordance with the set rules and requirements, companies shall find out the causes (i.e. the reasons of the nonconformity) and then take appropriate corrective or preventive measures. An example of corrective measure can be to increase the frequency of checking the relevant records. And an example of preventive measure can be to provide incentive program to encourage the compliance of the relevant rules and regulations. Pursuant to the requirements of Clause 8.3, enterprises should collect and analyze relevant information, such as the internal audit reports, results of the corrective measures taken, and the results of market/competitors analysis. The above information can be used as input information during management review (Clause 5.5.2 ) to decide whether it is required to amend or set new intellectual property management policies and objectives. Through continual auditing and revising, a systematic IP management system can be established. IV Conclusion In the era of knowledge economy, the abilities of most domestic enterprises to manage tangible assets have gradually matured (ex. ERP system). However, the abilities to manage intangible assets which include intellectual property have yet to be developed. Management systems in most domestic enterprises are fragmented. For example, legal departments are only responsible for contract reviewing tasks; R&D staff has limited IP knowledge. The importance of IP is often overlooked and most enterprises do not see that intellectual property management is the responsibility of every employee. As a consequence, the Taiwanese government establishes and promotes TIPS to encourage domestic enterprises to adopt a systemic approach of managing their intellectual property and TIPS is also provided as a tool to assist enterprises to establish a sound intellectual property management system. The purpose of implementing TIPS is not to request enterprises to establish a separate management system. In order to maintain efficiency and competitiveness, an enterprise has to have an integrated management system to support its core operations and also to meet the requirements of different management system standards. Eliminating overlaps of the requirements between different quality management systems is an inevitable trend. TIPS incorporates IP management with the ISO 9000 quality management system, which is capable of simplifying the complicated IP management tasks into an effective and standardized IP management system. TIPS helps an enterprise to establish a systematic process for managing its IP. Through competitive analysis, market trend analysis, and periodic IP management operations review, a company can revise and amend its IP management policies and goals and continually improve its IP management system. For example, sales departments shall collect market trends, competitive information and shall also consciously avoid acquiring materials that may raise infringement concerns. Human resource departments shall focus their efforts in providing IP education and training. Finance departments shall evaluate the costs required for maintaining the existing IP rights and inform the R&D departments to conduct relevant review at the appropriate time. R&D departments shall conduct prior art search before a new research project is commenced. TIPS offers a simple, efficient, and low-cost management system which assists an enterprise to establish an IP management system that aligns to its business goals and operation activities. We hope that by promoting and encouraging domestic enterprises to adopt and implement TIPS, Taiwan can strengthen its international competitiveness and sustain the growth of its economy and the whole society. 1.Taiwan Intellectual Property Management System (TIPS). The Ministry of Economics Affairs combined the IP management principles and the PDCA (Plan-Do-Check-Action) model used in ISO9001:2000 quality management system to create TIPS. The adoption of PDCA model helps organizations to establish a systematic and effective IP management system which can be continuously improved. 2. Chen Yi-Chih is a Section Manager at the Science and Technology Law Center ; Chen Hung-Chih is a legal Researcher at the Science and Technology Law Center . 3. Data Source: http://www.atmt.org.tw/html/modules/news/article.php?storyid=135&PHPSESSID=cab6428078a0435c5af1b2e7bbe2b121 (last visited: 08/11/2007 ) 4. Data Source: http://www.cyberone.com.tw/ItemDetailPage/PDAFormat/PDAFContent.asp?MMContentNoID=36372(last visited: 08/11/2007 ) 5. “Enterprise” as defined in TIPS includes company, corporate, school, research institute, a specific department or a project team is also included. 6. TIPS was developed based on the PDCA (Plan-Do-Check Action) model, a typical ISO management process which requires continuously monitoring, evaluating, analyzing and improving the whole system. 7. The TIPS guidelines can be found at: http://www.tips.org.tw/public/public.asp?selno=236&relno=236 8. Refer to article: New Philosophy of Intellectual Property – Use ISO Quality Management to establish a systematic IP management in Intellectual Property Journal, issue 74, 02/2005. 9. http://www.tips.org.tw/public/public.asp?selno=236&relno=236 (last visited: 08/12/2007 ) 10. The guidelines of TIPS also serve as the requirements for certification purpose. The Industrial Development Bureau of the Ministry of Economic Affairs will issue a certificate to an organization if such organization has implemented an IP management system satisfying the requirements of TIPS.
Taiwan Intellectual Property Survey Report 2023Taiwan Intellectual Property Survey Report 2023 2024/06/27 Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Institute for Information Industry has conducted the survey of “The Intellectual Property Survey Report” to listed companies since 2012. The Intellectual Property Survey Report 2023 on Taiwan's Listed and Over-the-Counter Companies was released in February 2024. Among the 331 publicly listed companies surveyed in 2023, the information technology sector had the largest representation, accounting for 44% (145 companies). This was followed by the manufacturing sector at 27% (90 companies), the pharmaceutical and livelihood sector at 18% (58 companies), and the industrial and commercial services sector at 11% (38 companies). Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig. 1 types of industry Based on the survey result, three trends of intellectual property management for Taiwanese enterprises have integrated with detail descriptions as below. Trend 1: Positive Growth in Intellectual Property Awareness and Intellectual Property Dedicated Department/Personnel, Budget and Projects 1. Taiwanese enterprises believe that intellectual property plays an important role More than 70% of companies believe that intellectual property can enhance product/service value, help profitability, and protect research results/core competitiveness. Specifically, 72% believe that intellectual property can enhance product/service value and help profitability, and 78% believe it can protect research results/core competitiveness. Additionally, 65% of companies believe that intellectual property can protect and enhance brand value, and 65% believe it can reduce the likelihood of disputes and infringements with others. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig.2 The benefit of intellectual property for the company 2.Taiwanese enterprises maintain investment in the dedicated department and full time personnel for intellectual property 33% of listed companies set up full time personnel for intellectual property and over 32% of those have established dedicated department to handle its business that is higher than 35% in 2023. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig.3 Department or personnel for intellectual property by year 3. Taiwanese enterprises plan budget for intellectual property each year 79% of enterprises have invested a certain amount of funds this year in acquiring, maintaining, and managing intellectual property. By industry, the information technology and pharmaceutical/livelihood sectors have a higher proportion of investment in related expenses, both exceeding 80% Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig. 4 fixed budget for intellectual property each year Trend 2: Taiwanese enterprises are willing to disclose their intellectual property information to the public, which can have a positive impact on the company. 1. Enterprises have a positive attitude towards disclosing intellectual property information. 72% of enterprises believe that disclosing intellectual property helps external parties objectively assess the company's value and competitiveness. This is followed by highlighting brand value (52%) and improving the internal management and control of intellectual property. By industry category, 77% of manufacturing companies believe it helps external parties objectively assess the company's value and competitiveness, which is higher than other industries. In the business services sector, 81% believe it helps highlight brand value, a significantly higher proportion. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig. 5 Benefits of disclosing intellectual property management information for enterprises 2. The main channels for public disclosure are company annual reports, sustainability reports, and intellectual property management plans The proportion of companies disclosing intellectual property plans in annual reports reaches 72%. Additionally, approximately 39% and 38% disclose in sustainability reports or intellectual property management plans, respectively. The proportion disclosed in company marketing and promotional materials is 29%, while the proportion in English-language sustainability reports is 20%. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig. 6 Channels for publicly disclosing corporate intellectual property management information Trend 3: Taiwanese enterprises use various types of intellectual property rights to protect their core competitiveness. 1. Trade secrets are considered crucial by enterprises but are less commonly owned forms of intellectual property Enterprises consider trademark rights, invention patents, utility model patents, and trade secrets to be more important, each with an importance score above 4. Design patents and copyrights are considered somewhat less important, each with an importance score of 3.8. However, there is a gap between the importance and the ownership rates of some types of intellectual property. The importance and ownership rates are consistent for trademarks, with an importance score of 4.5 and an ownership rate of 88%. Patents have an importance score of 4.7 and an ownership rate of 70%. Trade secrets have an importance score of 4.6 and an ownership rate of 49%. Copyrights have an importance score of 3.8 and an ownership rate of 30%. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig. 7 Owned and Importance of Various Intellectual Properties 2. The priority of using intellectual property rights varies across different industries Patents are used to protect important assets by the largest proportion of companies, about 86%. This is followed by trademarks at 77%, trade secrets at 66%, and copyrights at 33%. By industry, the order is consistent in information services, manufacturing, and pharmaceutical/livelihood industries: patents, trademarks, trade secrets, and copyrights. In the business services sector, the order is trademarks, trade secrets, patents, and copyrights. Data source: Innovation & Intellectual Property Center, Science & Technology Law Institute (STLI), Taiwan Intellectual Property Survey Report 2023. Fig.8 which type of intellectual property rights do companies use to protect important assets The complete survey report can be accessed in the Taiwan Intellectual Property Management System (TIPS) website. The download link is https://www.tips.org.tw/body.asp?sno=BGCHDC#460
A Preliminary Study on The Legal Effect of the Blockchain-Generated Data in TaiwanA Preliminary Study on The Legal Effect of the Blockchain-Generated Data in Taiwan I. Preface Governments around the world have set various regulations and guidelines to deal with the increasing application of blockchain technology, trying to keep the law up to date with technological development and the latest trends. Among them, the application of blockchain technology to regulations has become a hot topic. Because of its features, such as immutable, easy to verify and transparently disclosed, it can improve the efficiency of law enforcement and reduce cost. Moreover, decentralization and the verification mechanism generated by mathematical computation can avoid the disputes arising from the existing system, in which the mechanism is set up and controlled by independent institutions, and thus the credibility could be universal. The international trend also shows the importance attached to the application of blockchain technology in the legal field. In 2017, the “Legal Services Innovation Index”, a study conducted by the Michigan State University College of Law and Google evaluated the level of innovation of law firms according to the search data on innovation indicators of the world’s major law firms. Blockchain has the highest number of clicks among all indices, and the average number of clicks of blockchain is more than twice that of AI.[1] In addition, there are international cases regarding the connection between the blockchain technology and legal provisions as well as the real cases that used blockchain technology to handle legal matters.[2] An organization, such as the Global Legal Blockchain Consortium (GLBC), work with enterprises, law firms, software development units, and schools to study the standards formulation and application methods of the application of blockchain technology to law-related matters. [3] This article will first discuss the legal enforceability of data generated by the blockchain technology through international cases, then review Taiwan’s current status and the legal enforceability of the data generated by the blockchain technology and to explore possible direction for regulatory adjustment if the government intends to ease the restriction on the application of blockchain in the fields of evidence authentication and deposition. II. International cases 1. US case: adjust the existing regulations and recognize the enforceability of blockchain technology The amendment HB2417[4] to the Arizona Electronic Transactions Act (AETA) signed by Arizona in April 2017 defines the blockchain technology and smart contracts and recognizes their legal effect on signatures, records and smart contracts. HB2417 defines “blockchain technology” as a “distributed, decentralized, shared and replicated ledger, which may be public or private, permissioned or permissionless, or driven by “tokenized crypto economics or tokenless” and provides that the “data on the ledger” is protected with cryptography, is immutable and auditable and provides an uncensored truth.” It’s worth noting that although, by definition, the data is true, it is uncensored truth in nature, which emphasizes the originality of the data. A “smart contract” is an “event driven program, with state, that runs on a distributed, decentralized, shared and replicated ledger that can take custody over and instruct transfer of assets on that ledger.” Under the original AETA regulations, records or signatures in electronic form cannot be deprived of legal validity and enforceability merely because they are in electronic form. To eliminate the legal uncertainty of any blockchain related transactions and smart contracts related to digital assets, HB 2417 states that a signature that is secured through blockchain technology is considered to be in an electronic form and to be an electronic signature, and a record or contract that is secured through blockchain technology is considered to be in an electronic form and to be an electronic record. The statute also provides that smart contracts may exist in business, and a contract relating to a transaction may not be denied legal effect, validity or enforceability solely because that contract contains a “smart contract term.” This makes the enforceability of electronic signing and electronic transactions made by Arizona’s blockchain technology equivalent to that of the signature and contract made by the traditional written format. In the following year, the Ohio governor signed the amendment SB220[5] to the Uniform Electronic Transactions Act (UETA) in August 2018, which took effect from November. The focus of the amendment is the same as that in Arizona. Although, unlike HB 2417, SB220 does not define blockchain technology, the added content can still guarantee the enforceability of electronic signatures and contracts made by the blockchain technology. The focus of the two amendments in the US is to supplement and revise the laws and regulations made in the past so that they are applicable to the transaction method under blockchain technology and have the same effect as other recognized methods. This reduces the uncertainty related to blockchain technology at the regulatory and commercial application level, and is expected to attract the blockchain related companies, investors and developers. 2. Case of China: The enforceability of blockchain technology in evidence deposition is recognized in line with courts’ new type of judgment. In September 2018, the Supreme People's Court implemented “The Provisions on Several Issues Concerning the Trial of Cases by Internet Courts,”[6] in which Paragraph 2 of Article 11 mentions that where the authenticity of the electronic data submitted by a party can be proven through electronic signature, trusted time stamp, hash value check, blockchain or any other evidence collection, fixation or tamper-proofing technological means, or through the certification on an electronic evidence collection and preservation platform, the Internet court shall make a confirmation. It shows that the Internet court can recognize the evidence deposited by blockchain technology, and its enforceability is equivalent to that of other technologies if its authenticity can be proved. Paragraph 1 of the same article also proposes the basis for review and judgment on the relevant standards for the broad definition of electronic evidence recognition. “The authenticity of generation, collection, storage and transmission process of the electronic data shall be examined and judged, and the items to be reviewed include whether the hardware and software environments such as the computer system based on which electronic data is generated, collected, stored and transmitted are safe and reliable; whether electronic data originator and generation time are specified, and whether the contents shown are clear, objective and accurate; whether the storage and safekeeping media of electronic data are definite, and whether the safekeeping methods and means are appropriate; whether electronic data extractor and fixer, and electronic data extraction and fixation tools and methods are reliable, and whether the extraction process can be reproduced; whether the contents of electronic data are added, deleted, modified or incomplete, or fall under any other circumstance; and whether electronic data can be verified in specific methods.” The judgment is based on a clear review. It is a supplement to the notarization process, which was the solo judgment basis for the enforceability of digital evidence. In addition, the rules on proof are clearly set out in Article 9, which covers two situations: online and offline. For offline evidence, the parties can convert it into electronic materials by scanning, re-shooting and duplicating, and then upload it to the litigation platform. For online evidence, it can be divided into two situations. One is the online electronic evidence possessed by the party, which can be imported to the litigation platform by providing links or uploading materials. The other is that the Internet court can obtain the structural information of the relevant cases from the e-commerce platform operators, Internet service providers and electronic data deposition and retrieve platform, and import it to the litigation platform to directly provide the information to both parties so that they can select and prove their claims. In this way, the court can use technical means to complete the migration and visual presentation of information. Before the Supreme People's Court enforced the provisions, the Hangzhou Internet Court of China recognized the enforceability of electronic evidence under the blockchain technology when hearing a copyright dispute in June 2018. The court's judgment pointed out that after reviewing the impartiality, technical level and evidence preservation methods of the blockchain evidence deposit service provider, the enforceability of the evidence is recognized, and thus the case was deemed infringement.[7] Beijing Dongcheng District Court also reviewed the blockchain deposition technology in an infringement of information network communication in September of the same year, including data generation, deposition, preservation, and recognized the enforceability of electronic evidence made by the blockchain technology. The court adopted the electronic evidence[8]. The Beijing Internet Court allows evidence deposition of the litigation files and evidence uploaded to the electronic litigation platform through the Balance Chain of evidence deposition established by the blockchain technology when handling the litigation cases online. This can prevent tampering and ensure the safety of litigation while keeping possible litigation evidence to facilitate verification in the future. While the Balance Chain is going online, the supporting standards, including the Beijing Internet Court Electronic Evidence Platform Access and Management Standards, the Enforcement Rules of the Beijing Internet Court Electronic Evidence Platform Access and Management Standards, the Application Form for Beijing Internet Court Electronic Evidence Deposition Access and the Instruction on the Beijing Internet Court Electronic Evidence Deposition Access Interface, are released simultaneously. These supporting standards prescribe the requirement of receivers, the requirement for the electronic information system of the receiver and the requirement for the juridical application of the evidence platform in details from the practical point of view so that the potential receivers can interconnect in a compliant manner while ensuring the quality of the connected data. III. Taiwan’s current situation In the above cases, the United States amended the laws and regulations related to the electronic transaction by increasing the scope of the terms, such as electronic forms of records, signatures and transactions so that the records, signatures and transactions made by the blockchain technology is as effective as that of other technologies. According to Article 9 of the Taiwanese Electronic Signatures Act, the enforceability of the data generated by blockchain technology shall still be judged case by case in terms of the technology for electronic documents, signature and transaction formation, and its applicability or exclusion shall be determined by laws or administrative agencies. In China, the role of electronic data is discussed in the relevant standards used by the Internet Court to examine the cases. Regarding the definition of electronic materials, electronic records and electronic documents, Paragraph 1 of Article 2 of the Taiwanese Electronic Signatures Act defines electronic document as a record in electronic form, which is made of “any text, sound, picture, image, symbol, or other information generated by electronic or other means not directly recognizable by human perceptions, and which is capable of conveying its intended information.”[9] In addition, Article 4 states “With the consent of the other party, an electronic record can be employed as a declaration of intent. Where a law or regulation requires that information be provided in writing, if the content of the information can be presented in its integrity and remains accessible for subsequent reference, with the consent of the other party, the requirement is satisfied by providing an electronic record. By stipulation of a law or regulation or prescription of a government agencies, the application of the two preceding paragraphs may be exempted, or otherwise require that particular technology or procedure be followed. In the event that particular technology or procedure is required, the stipulation or prescription shall be fair and reasonable, and shall not provide preferential treatment without proper justifications.” [10] The electronic records, regardless of the type of technology, are given the same effect as paper documents with the consent of both parties. In litigation, electronic records, electronic evidence or similar terms are not found in the Criminal Code of the Republic of China, the Civil Code, the Code of Criminal Procedure and the Taiwan Code of Civil Procedure. The adoption of electronic records often refers to Paragraph 2 of Article 220 of the Criminal Code of the Republic of China[11]. An audio recording, a visual recording, or an electromagnetic recording and the voices, images or symbols that are shown through the computer process and are sufficient evidence of intention shall be considered a document. The content that is considered meaningful is that the identity of the person expressing the content is identifiable according to the content and can be used to prove legal relationship or fact in social life. The relevant standards for proof under the electronic evidence follow Article 363 of the Taiwan Code of Civil Procedure[12]. For non-documentary objects which operate as documents, including those are accessible only through technological devices or those that are practically difficult to produce their original version, a writing representing its content along with a proof of the content represented as being true to the original will be acceptable. However, the way of proof or recognition standards are not sufficiently described. Or according to Paragraph 2 of Article 159-4 of the Code of Criminal Procedure, “documents of recording nature, or documents of certifying nature made by a person in the course of performing professional duty or regular day to day business, unless circumstances exist making it obviously unreliable. In addition”, and Paragraph 3 “ Documents made in other reliable circumstances in addition to the special circumstances specified in the preceding two Items.” [13] In fact, the Juridical Yuan started to promote the electronic litigation platform (including online litigation) in 2016, and has launched the online litigation business by gradually opening the application for different types of applicants and litigation.[14] However, there is no description on the technical type and inspection standards of electronic evidence. Moreover, only the litigation evidence is uploaded. There is no evidence deposition before litigation for comparison during litigation. Under Taiwan’s laws and regulations, electronic evidence and its proving method is not significantly different from other types of evidence. The judgment of evidence shall still depend on judges’ recognition on the evidence. Taking the practice of criminal litigation as an example, it can be viewed at three levels[15]: 1. The submission of the evidence. If the evidence is collected illegally, not following a statutory method or is not logically related to the pending matters, it will be excluded. This is the way to determine whether the evidence is eligible to enter the evidence investigation process. 2. In the investigation of evidence, the method of investigation (e.g., whether it is legal), the determination of relevance and the debate on evidence (e.g., to confirm the identity of the person producing the electronic evidence, whether the electronic evidence is identical to the original version without addition, deletion or alteration) are investigated during the investigation procedure. 3. The debate on evidence is to determine the power of the evidence by considering the relationship among the elements that constitute the whole and whether the evidence can prove the connection among all elements. In addition, whether the electronic evidence is consistent with the original version is often based on Article 80 of the Notary Act, "When making notarial deeds, notaries shall write down the statements listened to, the circumstances witnessed, and other facts they have actually experienced. The means and results of the experience shall also be stated in the notarial deeds.” [16] A notary shall review the electronic evidence and record the inspection process and the inspection results to demonstrate its credibility. VI. Conclusions and recommendations According to the latest 2050 smart government plan[17] announced in the Executive Yuan’s 3632nd meeting held on December 27, 2018, the government is planning to connect the database of each government agency through blockchain technology, and the plan also includes establishment of digital identification. It is foreseeable that there will be more and more electronic materials, documents and records connected by blockchain technology in the future. When it comes to improve management efficiency and reduce the barriers to introduce this technology to various sectors, it is necessary to adjust the related regulations. At present, there are no statutory provisions for the technology that assist the use of the electronic evidence involved in traditional litigation channels or online platforms, including using blockchain for evidence deposition and authentication . This also poses uncertainty to the judges when they make judgments. If we consider the continuous development and breakthrough of technology, which is relatively faster than the legislative process, and the traditional tangible transactions and contracts are still the majority in life, Taiwan has defined electronic materials, electronic records and electronic documents in the Electronic Signatures Act to ensure and strengthen the legal rights and benefits under the adoption of the technology. In addition, the Electronic Signatures Act also reserves the right to determine whether the technology is applicable to the laws and regulations or administrative agencies. In other words, the technology behind electronic materials, records and documents are not specified, and the aforementioned electronic materials have the same effect as the contracts and signature as the traditional written format. However, there are no standards to specify which standards are valid for evidence deposition and authentication for electronic materials on the level of deposition and authentication. In the future, when improving the relevant functions of the online litigation platform, the Juridical Yuan can also consider using technologies, such as blockchain or timestamps to provide evidence deposition service, which is expected to enhance the efficiency of evidence verification for online litigation in the future and prevent wasting review resources on invalid evidence for a better operation mode. This is in line with the government's policy direction. By providing support and demonstration of emerging technologies, not only limited to blockchain, on the legal level, it can reduce the public’s uncertainty and risk on introducing or applying the technology to legal process. This is very helpful in realizing a large scale application of the technology. [1] Legal Services Innovation Index, Phase 1, Version 1.0, https://www.legaltechinnovation.com/law-firm-index/ (last visited on Jan. 11, 2019). [2] For example, Arizona's Arizona Electronic Transactions Act (AETA) and Ohio’s Uniform Electronic Transactions Act (UETA) described the electronic signature and the enforceability of contracts under blockchain technology; in China, Beijing Internet Court provides litigation files and litigation evidence deposition service based on blockchain technology for future litigation. [3] The Global Legal Blockchain Consortium website, https://legalconsortium.org/ (last visited on Jan. 11, 2019). [4] H.B. 2417, 53th Leg., 1st Regular. (AZ. 2017). [5] S.B. 220, 132ND General Assembly. (OH. 2017-2018). [6]“The Provisions on Several Issues Concerning the Trial of Cases by Internet Courts,” the Supreme People's Court of the People’s Republic of China http://www.court.gov.cn/zixun-xiangqing-116981.html (last visited on Jan. 11, 2019). [7] Tencent Research Institute, <The era of judicial blockchain has arrived? ——from the two cases of blockchain electronic deposition>, October 23, 2018, https://ek21.com/news/1/132154/ (last visited on Jan. 11, 2019). [8] Securities Daily, <Beijing Dongcheng District Court confirmed the evidence collection by blockchain for the first time-- application of "blockchain + justice" for new opportunities in history> October 20, 2018, https://www.jinse.com/bitcoin/258170.html (last visited on Jan. 11, 2019). [9] Paragraph 1 of Article 2 of the Electronic Signatures Act [10] Article 4 of the Electronic Signatures Act [11] Paragraph 2 of Article 220, “A writing, symbol, drawing, photograph on a piece of paper or an article which by custom or by special agreement is sufficient evidence of intention therein contained shall be considered a document within the meaning of this Chapter and other chapters. So shall be an audio recording, a visual recording, or an electromagnetic recording and the voices, images or symbols that are shown through computer process and are sufficient evidence of intention.” [12] Article 363 of the Taiwan Code of Civil Procedure, “The provisions of this Item shall apply mutatis mutandis to non-documentary objects which operate as documents. Where the content of a document or an object provided in the preceding paragraph is accessible only through technological devices or it is practically difficult to produce its original version, a writing representing its content along with a proof of the content represented as being true to the original will be acceptable. The court may, if necessary, order an explanation of the document, object, or writing representing the content thereof provided in the two preceding paragraphs.” [13] Paragraph 2 of Article 159-4 of the Code of Criminal Procedure [14] Liberty Times, <The Juridical Yuan is promoting “E-litigation.” Two new systems are on the road.” August 1, 2018, http://news.ltn.com.tw/news/society/breakingnews/2506118 (last visited on Jan. 11, 2019). [15] Chih-Lung Chen, “Seminar on the Reform of the Code of Criminal Procedure 3: Revision Direction of Rule of Evidence,” The Taiwan Law Review, Issue 52, Page 71-73 (1999). [16] Article 80 of the Notary Act. [17] BlockTempo, <The Executive Yuan Announced the Smart Government New Plan: the Taiwan Government will Use Blockchain Technology to Establish Information Exchange Mechanism of Various Agencies>, January 2, 2019, https://www.blocktempo.Com/taiwan-gv-want-to-use-blockchain-tech-build-data/ (last visited on Jan. 11, 2019).
The Development of Non-Drama TV Programs in Taiwan and the Protection of Intellectual Property RightsThe Development of Non-Drama TV Programs in Taiwan and the Protection of Intellectual Property Rights With the advancement of an era of digital content, the industrial structure of the audio-visual content industry has gradually changed. The production and sales channels of audio-visual content have appeared to trend toward diversification. Emerging content channels or new media have replaced traditional TV stations. The transmission speed of digitized content is faster than the traditional media, which has become an output opportunity for the content of Taiwan in the international market. In the field of drama programs, there have been cases of successful global output, and international cooperation and export models have been gradually discovered. By contrast, non-drama TV programs of Taiwan still remain in the traditional production mode in lack of creation of new content or funds, as well as talents for production and international marketing, which leads to a vicious circle of industrial stagnation or even regression. 1. Problems with domestic non-drama TV programs Funding is the first issue that needs to be resolved. "Due to the lack of money, the only thing that can be done is producing programs that no one wants to watch." Such a condition exists day after day that causes the entire non-drama programs to be depressed, and few people are willing to invest. By contrast, in China or South Korea, the linkage of its variety shows brings about the development of the content industry, and the benefits are amazing. The willingness to spend money on the investment at its initial stage is an essential element of success. However, if there is no successful case, it may not be easy to solely rely on Taiwanese private funds. As far as the technical level of TV program production is concerned, it is particularly important to modelize TV programs if they are to be exported. The market transaction of international TV program formats has existed for many years, but the object of the transaction is the core content and production process of TV programs, that is, the TV program bible. For non-drama TV programs of our country, if it needs to sum up the core of the program in one sentence, it is not impossible to achieve. However, it still lacks the core content such as the famous tv show "THE Voice" that is sufficient to attract people. In addition, in terms of production, how to edit as well as integrate the stage and supporting design into the shooting so to present attractive programs is the relatively lacking part in TV programs of our country. As for the cultivation of talents, Taiwan has yet rarely relevant talents who are able to research, develop, and independently write the TV program bible, as well as do marketing. By contrast, China has achieved remarkable results in TV programs in recent years. They have some consultant companies that specialize in writing a TV program bible for production companies. Their R&D personnel record details by following and observing the directors, producers, and photographers, of which the records gradually become a TV program bible. Some talents in China have mastered the art of writing TV program formats. They can even directly disassemble well-known foreign formats and rewrite them as Chinese versions for production, which has achieved success. 2. Overview of international TV program formats Taking a broad view of the status of foreign TV program formats, it is found that the output of creative development is not in the countries with big entertainment industries such as the United States, the United Kingdom, and France, but in small European countries such as the Netherlands and Israel, which have a large number of output of TV program formats. The Netherlands and Israel are not countries where the television industry is prosperous. However, their TV program output occupies an important position in the global market. Some programs have even produced more than 1,000 episodes in the world, with the output to countries including the United States, China and others. Similar to Taiwan, Netherlandish and Israeli TV programs are also faced with great limitations in production funds due to the small domestic market. However, many TV programs have been created by relying on the novel program content and taking full account of the needs of the international market. In the international trade market of TV program formats, if you intend to successfully output a program, it not only contains a novel main idea, but also covers production and viewing. The output carrier of TV program formats is the "TV Format Bible". Its content includes various links of program rundown, personnel settings, camera lenses, sound effects and lighting, etc. As long as the program has a fixed existing model, no matter who plays the roles in the program, the quality of the program can be kept stable. This kind of production of non-drama TV programs according to the TV Format Bible is called TV Format. 3. Protection of huge business opportunities of formats: preservation and authorization management of intellectual property rights The core value of formats often lies in the creative part of the content. How to effectively preserve the creativity and at the same time to claim the rights are of the most concern by ideators, and the carrier of modelizing creation is the "TV Format Bible". The writing of the "TV Format Bible" is based on the thinking of TV Format structure. At the creative stage, the core content will be integrated into the production level, including how to set up the lighting and the arrangement of the camera to achieve the entertainment effect of the creative core content and other details. However, the value of the "TV Format Bible" comes from the ideation of creativity, and whether creativity is to be protected by law has been controversial since always. Judging from the results of the current judgments on disputed cases concerning the TV Format, the more specific the TV Program Bible is written, the higher chance it has to be protected. A successful variety show not only can bring about the domestic and foreign income from the show itself, but associated derivatives such as music, tourism, and peripheral products may also be able to obtain huge business opportunities due to the broadcast of the program. Therefore, although the TV Program Format is centered on its content, it actually involves issues of industrial management such as human resources, labor relations, corporate governance, taxation, fundraising, bankruptcy procedures, economic systems, and professional ethics. In addition, in aspects of commerce, marketing and management aspects, matters such as the establishment of the production team, the production process management, the acquisition and use of creation funds, and valuation are all covered in the operation of formats.
- Impact of Government Organizational Reform to Scientific Research Legal System and Response Thereto (1) – For Example, The Finnish Innovation Fund (“SITRA”)
- The Demand of Intellectual Property Management for Taiwanese Enterprises
- Blockchain in Intellectual Property Protection
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System
- Recent Federal Decisions and Emerging Trends in U.S. Defend Trade Secrets Act Litigation
- The effective and innovative way to use the spectrum: focus on the development of the "interleaved/white space"
- Copyright Ownership for Outputs by Artificial Intelligence
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System

