The Research on Cybersecurity Risks in 5G network: Perspectives on Global strategy
The Research on Cybersecurity Risks in 5G network: Perspectives on Global strategy
I. The characteristics of 5G and cybersecurity threats
Compared to 4G, 5G adopts several new designs on the network architecture, such as software-defined networking (SDN), a baseband unit (BBU), logical disjunction, network function virtualization (NFV), and multi-access edge computing (MEC), to provide users with high-speed, low-latency and other quality services, as well as flexibility and expansibility to accommodate more emerging applications.
According to the three key usage scenarios (see Figure 1) defined by the International Telecommunication Union (ITU), enhanced mobile broadband access (eMBB) provides high-volume mobile broadband services such as AR/VR or ultra-high-definition video. Massive machine type communication (mMTC) provides large-scale IoT services. Ultra-reliability and low latency communication (uRLLC) can be used for services that require low-latency and high-reliability connections, including unmanned driving and industrial automation.
However, with 5G’s open, flexible and extensible design, as well as its coexistence with other 4G and 3G systems in the early stage of commercial operation, the cybersecurity threats facing 5G networks are more severe and diverse than the past mobile phone generations. At present, the known 5G cybersecurity threats mainly come from network functional components and connection interfaces among components, including the terminal device, access network, air interface, cloud virtualization, multi-access edge computing rental, core network, back-end/backbone network, roaming and external services, and so on.
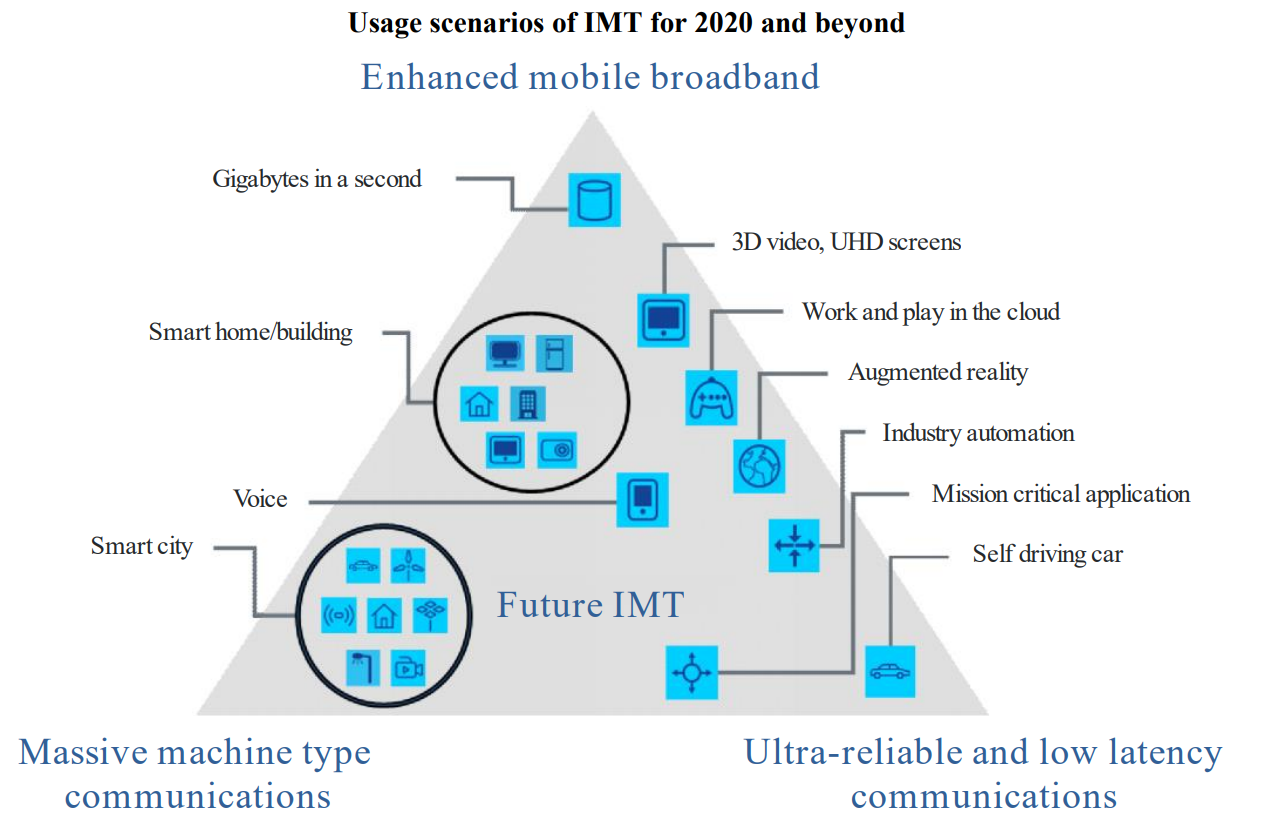
Source: ITU
Figure 1 Three key 5G scenarios by the ITU
II. Cybersecurity strategy development in major countries
5G is not only one of the critical infrastructures, but also an important foundation for pursuing a digital nation, digital economy, the industrial 4.0, and for promoting industrial transformation for upgrading. However, different scenarios require different cybersecurity protection levels, which poses great challenges to both mobile network operators and service providers.
Therefore, the construction of favorable environment for 5G development, the promotion of relevant applications and the development of innovative services and so on, have become the priority of governance in the countries around the world.
1. European Union (EU)
Then European Commission President Jean-Claude Juncker noted in 2017 that “Cyber-attacks can be more dangerous to the stability of democracies and economies than guns and tanks…Cyber-attacks know no borders and no one is immune,” indicating the EU's high priority in the cybersecurity field.
The "Digital Single Market," an important EU policy, lays the foundation for digital economy based on "cybersecurity, trust and privacy." In response to the loss of billions of euros a year in cyber attacks, the EU has taken a series of measures to safeguard and advance the development of the Digital Single Market. For the purposes of this strategy, the European Commission in 2018 came up with the policy of Resilience, Deterrence and Defence: Building strong cybersecurity for the EU,[1]with the aim of improving the level of cyber security, cyber resilience and trust in the EU, and in June 2019 passed the Cybersecurity Act [2] with two highlights described as follows:
(1) Strengthen the authority of the European Union Agency for Network and Information Security (ENISA)(see Figure 2), increase the allocation of human and financial resources to ENISA, as well as the preparation for the work items related to the cybersecurity industry, and reinforce cyber security support for EU member states.
(2) Establish the EU cybersecurity certification framework. [3]
In the European Union, where different cybersecurity certification schemes already exist, the absence of a common certification regime would increase the risk of fragmentation of the single market. For this reason, a set of technical requirements, standards and procedures are provided under this framework to assess whether information/communication products, services and processes are in compliance with security requirements.
The certification program includes product and service categories, information/communication security requirements (e.g. reference standards or technical specifications), types of assessment (e.g. self-assessment or third-party assessment), levels of security, and so on. All member states agree that certification not only facilitate cross-border business transactions, but also enable consumers to better understand the security of products and services.

Source: Compiled from the ENISA websit
Figure 2 ENISA organization and authority strengthening
2. the United States (U.S.)
In consideration of cyber security affairs in the country, the US Department of Homeland Security (DHS) in May 2018 unveiled the "Cybersecurity Strategy,"[4] which focused on the objectives and priorities of the U.S. government in future cybersecurity protection, identifying and managing national cybersecurity risks with the overall risk management approach, and addressing security threats to the country, critical infrastructures and private enterprises, as well as preventing cybercrimes.
Then the White House in September 2018 released the National Cyber Strategy of the United States of America, [5] based on the Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure [6] issued in May 2017, stating the strategy and position of the United States against the threat of cyber- attacks. The strategic goal aimed to, by safeguarding cybersecurity, protect the American people, the homeland, and the American way of life, to build a secure digital economic environment, to promote American prosperity, and strengthen cooperation with partners to deter malicious cyber attackers, so as to maintain peace and security, and continue to expand U.S. influence.
The department in July 2019 published the Digital Modernization Strategy [7] to announce its national defense strategy in the digital environment, including the use of cybersecurity, AI, cloud computing, blockchain and other technologies in information security protection to create a more secure, coordinated and efficient platform and improve the security of intelligence transmission and processing.
3. Canada
Public Safety Canada in June 2018 released the National Cyber Security Strategy, [8] with the vision of a sustainable, robust cybersecurity environment, innovation and prosperity. Through international cooperation and a domestic public-private partnership, the department has been working on three goals: 1. cyber security and resilience (to reduce cybercrime and ensure Internet privacy; 2. Internet innovation (to create a friendly environment for the development of cybersecurity startups); 3. government leadership and cooperation (to transfer government-owned cybersecurity knowledge to the private sector and set up a cybersecurity governance framework).
The Canadian government also attaches great importance to critical infrastructure. In May 2018, the National Cross Sector Forum 2018-2020 Action Plan for Critical Infrastructure [9] was unveiled to facilitate information sharing between public and private partners through sharing and protecting intelligence, and implementing a full risk management approach. Moreover, Public Safety Canada in April 2019 issued a report called Enhancing Canada’s Critical Infrastructure Resilience to Insider Risk, which provided guidelines and suggestions for action on internal risks in critical infrastructure organizations.[10]
4. Singapore
The government of Singapore in 2018 promulgated the Cybersecurity Act, [11] which aimed to fulfill the vision of a Smart Nation by enacting and putting into effect cybersecurity regulations to achieve the goal of a resilient infrastructure and a more secure cyberspace, and to strengthen the protection of critical information infrastructure against cyber-attacks. The Cyber Security Agency of Singapore (CSA) was given the authority to prevent and respond to cybersecurity threats, and to set up a system for sharing security information, as well as a light-touch licensing system for cybersecurity service providers.[12]
The Government of Singapore has appointed a Commissioner of Cybersecurity responsible for promoting domestic cybersecurity policy. To safeguard Singaporeans from cybersecurity threats, [13] the government particularly laid down cybersecurity threat or incident response provisions in Chapter 4 of the Cybersecurity Act to empower the Commissioner of Cybersecurity to investigate cybersecurity threats and incidents, such as requiring the parties to the incidents to present statements in person or in writing, producing documents or provide information and so on.[14]
5. Australia
The Australian government in 2016 proposed a four-year "Australia's Cyber Security Strategy,"[15] which was expected to invest more than 230 million Australian dollars to strengthen Australia's cyber security capability and complete the following five aspects: national cyber partnership, strong cyber defenses, global responsibility and influence, growth and innovation, and a cyber smart nation.
As for the global responsibility and influence, the Australian government in 2017 announced the "Australia's International Cyber Engagement Strategy."[16] which aims to strengthen digital trade, to improve cybersecurity and to response to cybercrime through international cooperation; encourage innovative cybersecurity solutions; provide security advice and best practices, such as Essential Eight strategies[17] to mitigate cyber-attacks; establish the Pacific Cyber Security Operational Network (PaCSON) [18] with neighboring countries to develop regional cybersecurity capabilities; and advance the development of Australia's cybersecurity industry, nurture startups and attract foreign investment.
III. Cybersecurity strategy to promote 5G in Taiwan
Since President Tsai Ing-wen took office in 2016, she declared that cybersecurity is directly linked to national security. In 2017, the Department of Cyber Security (DCS) under the Executive Yuan issued "National Cybersecurity Development Plan (2017-2020)," and in 2018 the "Cybersecurity Industry Development Action Plan (2018-2025)," in order to enhance the independence of Taiwan's cybersecurity industry, consolidate the nation’s cybersecurity defense line, improve its innovative thinking of cyber security, and further promote it to the international market.
To develop a favorable environment to promote 5G, the Executive Yuan on May 10, 2019 approved the “Taiwan 5G Action Plan (2019-2022),” [19] with a total investment about NT$20.466 billion over a four-year period. The plan aims to build a 5G application and industrial innovation environment, and reshape Taiwan's mobile communication industry ecosystem, with its content planned around five themes, including "promoting 5G vertical application field demonstration", "building 5G innovation and application development environment," "completing 5G technology core and cybersecurity protection capabilities," "planning to release 5G frequency spectrums in line with overall interests" and "adjusting laws and regulations to create favorable environment for 5G development," and to promote industrial upgrading and transformation, as well as create the next wave of economic prosperity in Taiwan.
Secure, robust and reliable 5G systems are sufficient and requisite conditions for building an innovation ecosystem in digital countries. The third theme of the "Taiwan 5G Action Plan" is to "complete 5G technology core and cybersecurity protection capabilities," which is intended to advance the integration of applied science and technology by establishing advantageous core technologies, set up a 5G technology and test platform, and increase the market competitiveness of 5G industry, while drafting the overall national policies on 5G cybersecurity, building the cybersecurity protection mechanism of 5G homemade products, strengthening 5G critical infrastructure and operational cybersecurity protection capabilities, and promoting domestic suppliers to enter the international 5G reliable supply chain.
In terms of strengthening 5G critical infrastructure and operational cybersecurity protection capacities, the NCC has planned a four-year (2019-2022) "5G Network Cybersecurity Protection and Related Regulations Preparation Plan." In coordination with a 5G license issue in 2020, the agency in 2019 added/amended the 5G cybersecurity provisions of the Regulations for Administration of Mobile Broadband Businesses, making it mandatory for the winning bidder of the 5G frequency spectrum to incorporate the cybersecurity protection concept into the system design for system construction.
Upon commercial operation of 5G, the NCC will audit from time to time the implementation of the cybersecurity maintenance plan by telecom operators, so as to ensure and reinforce the cybersecurity protection system of Taiwan's 5G telecom network, and create an opportunity for the development of 5G homemade products with cybersecurity protection capability. In addition, the NCC will also face up to the fact that 5G technology standards continue to evolve, and the operators have different construction schedules and heterogeneous mobile networks coexist. Therefore, relevant regulations will continue to be completed from 2020 to 2022, and examples will be verified through cybersecurity function testing laboratories to ensure that cybersecurity protection functions of 5G networks keep pace with the times.
IV. Conclusion and Suggestion
As for emerging technologies, countries around the world are actively evaluating and constructing 5G systems and services. Taiwan boasts excellent industrial advantages in terms of semiconductors, ICT software and hardware, and high-quality talents, and thus makes a foundation for developing 5G. Furthermore, going with the importance of cybersecurity, it is necessary to pay more attention to planning and developing 5G cybersecurity technology.
It is clear that the development of cybersecurity is both a challenge and an opportunity for Taiwan. In order to implement the national policy objectives of "cybersecurity is national security" as well as "innovative economic development programs for a digital nation," and to response to the scientific and technological progress, and the demand for cybersecurity, key development direction is proposed to expedite the establishment of 5G cybersecurity protection.
Reference:
[1]Resilience, Deterrence and Defence: Building strong cybersecurity in Europe, European Commission, https://ec.europa.eu/digital-single-market/en/news/resilience-deterrence-and-defence-building-strong-cybersecurity-europe
[2]The draft Regulation of The European Parliament And of The Council on ENISA, the "EU Cybersecurity Agency", and repealing Regulation(EU)526/2013, and on Information and Communication Technology cybersecurity certification(''Cybersecurity Act'') was published in September 2017 to expand the rights and obligations of ENISA, which would make ENISA the EU's cybersecurity and information competent authority and the authority for critical infrastructure (information) facilities after the passage of the Act.
Regulation (EU) 2019/881 of the European Parliament and of the Council of 17 April 2019 on ENISA (the European Union Agency for Cybersecurity) and on information and communications technology cybersecurity certification and repealing Regulation (EU) No 526/2013 (Cybersecurity Act) (Text with EEA relevance), https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=uriserv:OJ.L_.2019.151.01.0015.01.ENG&toc=OJ:L:2019:151:TOC
[3]The EU cybersecurity certification framework, European Commission, https://ec.europa.eu/digital-single-market/en/eu-cybersecurity-certification-framework
[4]Cybersecurity Strategy(2018), DHS, https://www.dhs.gov/sites/default/files/publications/DHS-Cybersecurity-Strategy_1.pdf
[5]National Cyber Strategy of the United States of America(2018), The White House, https://www.whitehouse.gov/wp-content/uploads/2018/09/National-Cyber-Strategy.pdf
[6]THE WHITE HOUSE, Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, The White House, https://www.whitehouse.gov/presidential-actions/presidential-executive-order-strengthening-cybersecurity-federal-networks-critical-infrastructure/
[7]DoD Digital Modernization Strategy, DoD, https://media.defense.gov/2019/Jul/12/2002156622/-1/-1/1/DOD-DIGITAL-MODERNIZATION-STRATEGY-2019.PDF
[8]National Cybersecurity Strategy, Public Safety Canada, https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/ntnl-cbr-scrt-strtg/index-en.aspx
[9]National Cross Sector Forum 2018-2020 Action Plan for Critical Infrastructure, Public Safety Canada, Public Safety Canada, https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/pln-crtcl-nfrstrctr-2018-20/index-en.aspx#a02
The action plan is a three-year program under Canada's2010 National Strategy for Critical Infrastructure (National Strategy) starting in 2010 for all phases.
[10]Enhancing Canada’s Critical Infrastructure Resilience to Insider Risk, Public Safety Canada, Public Safety Canada, https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/nhncng-crtcl-nfrstrctr/index-en.aspx
[11]Cybersecurity Act 2018, Singapore Statutes Online, https://sso.agc.gov.sg/Acts-Supp/9-2018/
[12]Cybersecurity Act, CSA, https://www.csa.gov.sg/legislation/cybersecurity-act
[13]Id.
[14]Cybersecurity Act Explanatory Statement, https://www.csa.gov.sg/~/media/csa/cybersecurity_bill/cybersecurity%20act%20-%20explanatory%20statement.pdf
[15]Australia’s Cybersecurity Strategy, https://cybersecuritystrategy.homeaffairs.gov.au/
What is the Government doing in cybersecurity, Ministers for the Department of Industry, Innovation and Science, https://www.industry.gov.au/data-and-publications/australias-tech-future/cyber-security/what-is-the-government-doing-in-cyber-security
[16]Australia’s International Cyber Engagement Strategy, Department of Foreign Affairs and Trade,https://www.dfat.gov.au/sites/default/files/DFAT%20AICES_AccPDF.pdf
[17]Essential Eight Explained, ACSC, https://www.cyber.gov.au/publications/essential-eight-explained
[18]Pacific Cybersecurity Operational Network(PaCSON), https://dfat.gov.au/international-relations/themes/cyber-affairs/cyber-cooperation-program/Pages/pacific-cyber-security-operational-network-pacson.aspx
Or Strengthening cybersecurity across the Pacific, ACSC, https://www.cyber.gov.au/news/pacific-islands
PaCSON is comprised of 15 members, including Australia, Fiji, Marshall Islands, New Zealand, Papua New Guinea, Samoa, and Solomon Islands.
[19]Taiwan 5G Action Plan, Executive Yuan,https://www.ey.gov.tw/Page/5A8A0CB5B41DA11E/087b4ed8-8c79-49f2-90c3-6fb22d740488
- Resilience, Deterrence and Defence: Building strong cybersecurity in Europe
- Regulation (EU) 2019/881 of the European Parliament and of the Council of 17 April 2019 on ENISA (the European Union Agency for Cybersecurity) and on information and communications technology cybersecurity certification and repealing Regulation (EU) No 526/2013 (Cybersecurity Act) (Text with EEA relevance)
- The EU cybersecurity certification framework
- Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure
- National Cybersecurity Strategy
- National Cross Sector Forum 2018-2020 Action Plan for Critical Infrastructure
- Enhancing Canada’s Critical Infrastructure Resilience to Insider Risk
- Cybersecurity Act 2018
- Cybersecurity Act
- Australia’s Cybersecurity Strategy
- What is the Government doing in cybersecurity
- Essential Eight Explained
- Pacific Cybersecurity Operational Network(PaCSON)
- Strengthening cyber security across the Pacific
- Taiwan 5G Action Plan
Whereas the burden of private nursing for the elderly is getting heavier, industrialized countries with an aging society are endeavoring to seek possibilities of reducing the unit healthcare cost, such as technology assistance, and even the introduction of the brand new care type or model, which is an emerging application field of increasing importance. The development of such kind of healthcare industry not only is suitable for aging societies but also coincides with the growing health management trend of modern people. Also, while the focus on acute diseases in the past has changed to chronic diseases which are common to most citizens, the measuring and monitoring of physiological indicators, such as blood pressure, pulse, blood sugar and uric acid have critical effects on condition control. However, it will mean huge financial and physical burdens to the elderly or suffering from chronic diseases if they need to travel to hospitals to measure these physiological indicators. At this moment, an economical, reliable and timely physiological information collection and transfer system will be technology with good potential. For this reason, the purpose of this study is to investigate the potential business opportunities by applying the emerging information technology (IT) to the healthcare industry and the derivative legal and regulatory issues, with a focus on the seamless healthcare industry. It is hoped that by assessing the opportunity and risk in terms of legal and strategic analysis, we can single out the potential imbalance of fitting seamless healthcare, an IT-enabled service (ITeS), in the conventional control framework, and thereby establish a legal environment more appropriate for the development of the seamless healthcare industry. Referring to the existing electronic healthcare classification, the industry is divided into the following four blocks: electronic content provider, electronic product provider, electronic linking service provider and electronic passport service provider. Also, by depicting the outlook of the industry, the mode of application and the potential and common or special legal problems of different products are clarified. Given that health information collected, stored and transferred by electronic means involves unprecedented risk in information privacy and security, and that the appropriate control of such risk will affect the consumer’s faith in and willingness to subscribe seamless healthcare services, this study analyzed the privacy framework of the USA, the EU and Taiwan. Results indicate that future privacy legislation in Taiwan should include the protection for non-computer-processed personal information, expand the scope and occupation of applications, reinforce control incentives, and optimize the privacy protection mechanism. Further, only when service providers have the correct and appropriate concept of privacy protection can the watch-and-wait attitude of consumers be eliminated. These can help to promote subsequent development of the industry in the future. Due to the booming international trade as a result of globalization, and the gradual opening of the domestic telecommunication and healthcare markets following Taiwan’s entry into the WTO, transnational distance healthcare will gradually become a reality. However, the determination of the qualifications of practitioners is the prerequisite of transnational healthcare services. Taiwan may also consider lowering the requirements for physicians to practice in other countries and thereby to enhance the export competitiveness of Taiwan’s healthcare industry by means of distance healthcare via endorsement or reciprocity. Lastly, whereas the risks distance healthcare involves are higher than conventional healthcare services, the sharing of burdens and disputes over applicable laws in case of damages are the gray areas for executive control or judicial practice intervention. For this reason, service providers are unwilling to enter the market because the risks are too unpredictable. Therefore, this study recommends that the insurance system for distance healthcare should be the focus of future studies in order to promote the development of the industry.
The Organization Framework, the Notification System and the Legal Norms of Critical Infrastructure Protection in the U.S.1. Organization Framework In the organization framework of critical infrastructure protection, there are mainly the public departments and the PPP organizations. The functions and task description of relevant organizations are as follows. (1) Department of Homeland Security After the September 11 attacks in America, the Homeland Security Act was passed in November 2002, and based on this act, 23 federal organizations, plans and offices were integrated to establish the Department of Homeland Security (DHS) to take responsibility for homeland security in America. The tasks include: (1) to analyze intelligence data collected from various departments such as the Central Intelligence Agency (CIA) and the Federal Bureau of Investigation (FBI) so that any threats to security can be discovered in time, (2) to protect and defend critical infrastructure, (3) to coordinate and lead America to prevent and respond to the attacks from nuclear weapons, biochemical weapons and other and (4) to coordinate the tasks of the federal government, including emergency and rescue. For the task regarding critical infrastructure and critical information infrastructure protection, the main units in charge are the Office of Infrastructure Protection (OIP) and the Office of Cybersecurity and Communications (CS&C) subordinate to National Protection and Programs Directorate (NPPD), Department of Homeland Security (DHS), to reduce the risk in both physical and cyber security to maintain national security1 (2) Congress Relevant units and committees are established both in the Senate and the House of Representatives to be responsible for protection and making policies pertinent to important critical infrastructure and critical information infrastructure. (3) Computer Crime and Intellectual Property Section In 1991, the Department of Justice (DOS) established the Computer Crime and Intellectual Property Section (CCIPS), a section of the Criminal Division, to be responsible for all crime combating computer and intellectual property. Computer crime is referred to cases which include electronic penetrations, data thefts, and cyber attacks to the important critical infrastructure. CCIPS also prevents, investigates, and prosecutes computer crimes by working with other government agencies, the private sector, academic institutions, and foreign counterparts. (4) Other Relevant PPP Organizations 2The Information Sharing and Analysis Center (ISAC) is responsible for the information security message sharing among the industries of each critical infrastructure to ensure the liaison and cooperation among industries. Finally, for the issue on critical information infrastructure, especially cyber crimes, both the National Cyber Security Alliance (NCSA) and the Cross Sector Cyber Security Working Group (CSCSWG) are designated to serve as crucial roles in governmental and non-governmental internet security prevention to be responsible for techniques and education. 2. Notification System (1)Computer Emergency Response Team Coordination Center The Computer Emergency Response Team Coordination Center (CERT/CC) run by Carnegie Mellon University is the oldest and most important early-warning organization for information security in the USA. With its experts studying internet vulnerabilities and risk assessment released regularly, it reminds people of the possible dangers which exist in the information age and the need to improve internet security. (2)US Computer Emergency Readiness Team The US Computer Emergency Readiness Team (US-CERT) was established in 2003. It is responsible for protecting the infrastructure of the internet in America and for coordinating and providing response support and defense against national cyber attacks. It interacts with federal agencies, industry, the research community, state government, and others to disseminate reasoned and actionable cyber security information to the public. (3)Federal Bureau of Investigation The Federal Bureau of Investigation (FBI), the first early warning center of critical infrastructure at the national level, is responsible for providing the information pertinent to legal execution presently and also taking responsibility for the investigation of cyber crime. (4)Information Sharing and Analysis Centers Currently, industry in America, including finance, telecommunications, energy, traffic, water resources, together established individual Information Sharing and Analysis Centers (ISACs) based on the policy made in PDD-63. The ISAC of the financial system established in October 1999 being the first established center. These ISACs further work together to form an ISAC Council to integrate the information from each of them and improve their interaction and information sharing. 3. Legal Norms In reference to the laws and regulations of critical infrastructure protection, America has aimed at critical infrastructure protection and computer crime to formulate the following regulations. (1) Federal Advisory Committee Act of 1972 According to the Federal Advisory Committee Act (FACA), the advisory committee can be established in every federal agency to provide the public, along with received open advice, with relevant objectives, and to prevent the public from being inappropriately influenced by the policies made by the government. However, to keep the private institutions which run the critical infrastructures from worrying the inappropriate leak of the sensitive information provided and consulted by them, Critical Infrastructure Partnership Advisory Council was established so that the Secretary of Homeland Security has the right to disregard the regulations of FACA and establish an independent advisory committee. (2) Computer Fraud and Abuse Act of 19863 The Computer Fraud and Abuse Act (CFAA) was enacted and implemented in 1986. It mainly regulates computer fraud and abuse. The Act states that it is against the law for anyone to access a protected computer without authorization. However, it also recognizes the fact that accessing a computer system of electronic and magnetic records does not mean a violation of the law. According to the CFAA, what is needed is one of the following requirements to be the wrongful conduct regulated in the Act: (1) whoever intentionally accesses a computer to obtain specific information inside the government or whoever has influenced the transmission function of the computer system; (2) whoever intentionally accesses a computer to obtain a protected database (including the information contained in a financial record of a financial institution or of a card issuer, or the information contained in a file of a consumer reporting agency on a consumer, or the information from any department of agency of the United States, or the conduct involving an interstate transaction); (3) whoever intentionally accesses any nonpublic computer of a department or agency of the United States, and causes damage. In addition, the Act also prohibits conduct such as transmitting malicious software, and defrauding traffic in any password or similar information. For any person who suffers damage or loss by reason of a violation of the law, he/she may maintain a civil action to obtain compensatory damages and injunctive relief or other equitable relief. However, the Computer Abuse Amendment Act (1994) expands the above Act, planning to include the conduct of transmitting viruses and malicious program into the norms whose regulatory measures were adopted by the USA Patriot Act enacted in October 20014 (3) Homeland Security Act of 20025 The Homeland Security Act provides the legal basis for the establishment of the Department of Homeland Security and integrates relevant federal agencies into it. The Act also puts information analysis and measures of critical infrastructure protection into the norm. And, the norm in which private institutions are encouraged to voluntarily share with DHS the information security message of important critical infrastructure is regulated in the Critical Infrastructure Information Act: Procedures for Handling Critical Infrastructure Information. According to the Act, the DHS should have the obligation to keep the information provided by private institutions confidential, and this information is exempted from disclosure by the Freedom of Information Act. (4) Freedom of Information Act Many critical infrastructures in America are regulated by governmental laws, yet they are run by private institutions. Therefore, they should obey the law and provide the government with the operation report and the sensitive information related with critical infrastructure. However, knowing that people can file a request at will to review relevant data from the government agencies based on the Freedom of Information Act (FOIA), then the security of national critical infrastructure may be exposed to the danger of being attacked. Therefore, the critical infrastructure, especially the information regarding the safety system, early warning, and interdependent units, are all exempted by the Freedom of Information Act. (5) Terrorism Risk Insurance Act of 20026 After the 911 Incident, Congress in America passed the Terrorism Risk Insurance Act to establish the mechanism to underwrite terrorism risk insurance, in which insurance companies are required to provide terrorism attack risk insurance and the federal government will also cover part of loss for severe attacks. 1.http://www.dhs.gov/xabout/structure/editorial_0794. shtm (last accessed at 21. 07. 2009). 2.http://www.thei3p.org/ (last accessed at 21. 07. 2009). 3.http://www.panix.com/~eck/computer-fraud-act. html (last accessed at 21. 07. 2009). 4.Mark G. Milone, Hacktivism:Securing the National Infrastructure, 58 Bus. Law, 389-390, 2002. 5.http://www.dhs.gov/xlibrary/assets/hr_5005_enr.pdf (last accessed at 21. 07. 2009). 6.http://www.ustreas.gov/offices/domestic-finance/financial-institution/terrorism-insurance/pdf/hr3210.pdf (last accessed at 21. 07. 2009).
The amendment of the Taiwanese Personal Data Protection ActThe amendment of the Taiwanese Personal Data Protection Act 2025/05/28 On March 27, 2025, the Executive Yuan released and submitted a draft partial amendment of the Personal Data Protection Act to the Legislative Yuan. The amendment aims to comprehensively enhance personal data protection by constructing the foundation for an independent supervisory agency[1]. Taiwan’s Personal Data Protection Act- legislative progress Taiwan’s Personal Data Protection Act (PDPA) has been amended three times since its release in 1995. In May 2023, the latest amendment to the PDPA introduced Article 1-1, designating the Personal Information Protection Committee as the competent authority under the Act. This legislative development was made in light of the Taiwan Constitutional Court Judgment 111-Hsien-Pan-13 (2022) (Case on the National Health Insurance Research Database)[2], which held that, to ensure the protection of personal information and the constitutional right to privacy under Article 22, the establishment of an independent data protection mechanism is required. In accordance with Taiwan Constitutional Court Judgment 111-Hsien-Pan-13 (2022), the Personal Data Protection Commission (PDPC) must be established by August 2025. To facilitate this, the Preparatory Office of the Personal Data Protection Commission was established in December 2023. This office is mainly responsible for drafting and establishing the regulations and organizational framework required to establish the independent authority, including drafting the Organization Act of the PDPC and the amendments to the PDPA. To develop the regulatory framework for an independent authority, the Preparatory Office of the Personal Data Protection Commission has planned a two-stage amendment process. The first phase seeks to establish the legal foundation of the PDPC, while the second phase will address other substantive issues of personal data protection. For the first stage, the Preparatory Office of the Personal Data Protection Commission drafted the Organization Act of the Personal Information Protection Committee in accordance with Article 1-1 of the PDPA and revised partial provisions of PDPA to reflect the function and duties of the PDPC. The Draft of Partial Amendment to the Personal Data Protection Act The key points of the amendment of PDPA are to empower the commission with essential regulatory functions, to strengthen the regulatory oversight and management of personal data within public sectors, and to set up a transition period to transfer regulatory authority over the private sectors[3]. 1. Empower the commission with essential regulatory functions Due to the lack of a unified agency for receiving incident reports and the efficiency issues caused by the current decentralized legal enforcement, the amendment of PDPA designates the PDPC as the competent authority to receive the incident reports. Centralizing incident reporting under the PDPC facilitates a clearer understanding of the nature and status of related incidents. It also helps regulatory authorities to investigate and handle problems quickly. The rules for reporting data breach incidents are set out in Article 12 of the amended PDPA. According to Article 12 of the amended PDPA, both public sector and private sector entities are required to take appropriate actions and retain the records when a data breach occurs. In addition, public sector entities must report the incident to the PDPC and other relevant government agencies, while private sector entities are required to notify the incident to the PDPC, which will then inform its competent authority[4]. In terms of personal data security maintenance, the amended PDPA states that the competent authority is responsible for formulating regulations concerning security maintenance, governance mechanisms, protective measures, and other relevant matters[5]. Accordingly, PDPC, as the competent authority, will draft the Regulations Governing Security Maintenance and Administration to provide the legal basis for the conducting audits, inspections, and administrative sanctions[6]. 2. Strengthen the regulatory oversight and management of personal data within the public sector The amendment of PDPA designates the PDPC as the independent authority responsible for overseeing the overall personal data protection affairs, including supervision of public sectors. The PDPC is empowered to supervise the public sector entities regarding their compliance with personal data protection regulations. Therefore, the role of the Data Protection Officer (DPO) is introduced in Taiwan for the first time. Article 18 of the amended PDPA states that every public sector entity must appoint a DPO to promote and oversee matters related to personal data protection. This approach reinforces personal data protection from both internal and external perspectives[7]. In considering restructuring and resource allocation associated with introducing this new role, the DPO requirement in PDPA currently applies to the public sector entities. However, both the public and private sectors are required to designate specialists to be responsible for managing personal data protection and security affairs[8]. 3. Set up a transition period to transfer regulatory authority over the private sectors Under the current regulation framework, the supervision of personal data protection in the private sector is decentralized and supervised by different competent authorities. To address this gap, the amendment of PDPA clarifies that the PDPC will serve as the supervisory authority for these entities in the future. In terms of the private sector entities already under the supervision of specific competent authorities, supervisory arrangements will initially remain unchanged. However, to achieve regulatory consistency, the amendment introduced a six-year transitional period during which supervisory responsibility will be transferred to the PDPC. During this transition, the PDPC will collaborate with relevant agencies every 2 years to assess the implementation of the new framework of PDPC and the situation of supervision across the private sector[9]. The draft Organization Act of the Personal Data Protection Committee has also been released To complete the legal basis of PDPC, the draft Organization Act of the Personal Data Protection Committee (hereinafter referred to as the draft of the Organization Act) is released with the PDPA amendment. The draft of the Organization Act aims to formalize the PDPC as the independent central supervisory body. Additionally, it also clarifies the division of responsibilities among agencies on personal data-related matters. Once enacted, the PDPC will serve as Taiwan’s independent authority. According to the draft of the Organization Act, the PDPC is designed as a collegial system with 5-7 committee members, serving a term of 4 years, and members may be reappointed upon completion of their term[10]. As a central third-level agency, the committee members will exercise their powers independently. The draft of the Organization Act states that the PDPC is responsible for making the legislation and policies of personal data protection, the oversight of personal data protection, promoting and researching personal data-related technology, protecting cross-border transfer of personal data and the talent acquisition of personal data protection[11]. The draft of the Organization Act establishes the legal foundation for the PDPC, outlining its organization structure and core responsibilities. Additionally, it grants the PDPC the authority to supervise and enforce compliance with personal data protection regulations. Benefits of the legal reform of the Personal Data Protection Act and the next step The draft partial amendment to the Personal Data Protection Act, along with the draft Organization Act of the Personal Information Protection Committee, have been submitted to the Legislative Yuan for legislative review. This marks the first time that Taiwan has established an independent authority responsible for personal data protection. The PDPA amendment not only formalizes the legal status and authority of the Commission but also enhances the legitimacy and credibility of personal data collection and use. However, amendments to other substantial aspects of data protection will be introduced in the next phase. The Preparatory Office of the Personal Data Protection Commission has already initiated work on the second phase, which will focus on substantial personal data protection issues in the context of the digital era. Reference: [1]The Executive Yuan approved the draft Organizational Act of the Personal Data Protection Commission and the draft of partial amendments to the Personal Data Protection Act, aiming to establish a comprehensive independent supervisory mechanism and enforcement authority, and to build robust data governance for the era of comprehensive AI application., Executive Yuan, https://www.ey.gov.tw/Page/9277F759E41CCD91/747cda78-926f-4205-99b3-1a735fc1b97b (last visited May. 19, 2025). [2]Constitutional Court Judgment 111-Hsien-Pan-13 (2022) (Case on the National Health Insurance Research Database). [3]Establish an independent supervisory authority for personal data protection to strengthen personal data safeguards. The Executive Yuan approved the draft Organization Act of the Personal Data Protection Commission and the draft partial amendments to the Personal Data Protection Act., Preparatory Office of the Personal Data Protection Commission website, https://www.pdpc.gov.tw/News_Content/20/907/ (last visited May. 19, 2025). [4]Partial Amendment Draft to the Personal Data Protection Act, the 8th meeting of the 3rd session of the 11th Legislative Yuan, General Bill No.20, Executive Yuan Proposal No.11010550, Art. 12. [5]Id. Art 18, Art 20-1. [6]Supra note 3. [7]Id. Art.18. [8]Id. Art. 20-1. [9]Id. Art.51-1. [10]Draft of the Organization Act of the Personal Information Protection Committee, the 8th meeting of the 3rd session of the 11th Legislative Yuan, General Bill No.20, Executive Yuan Proposal No. 1101052, Art. 3.Draft of the Organization Act of the Personal Information Protection Committee, the 8th meeting of the 3rd session of the 11th Legislative Yuan, General Bill No.20, Executive Yuan Proposal No. 1101052, Art. 3. [11]Id. at Art. 2.
Introduction to Critical Infrastructure ProtectionThe security facet of cyberspace along with a world filled with CPU-controlled household and everyday items can be examined from various angles. The concept of security also varies in accordance with different stages of national conditions and industrial development in different nations. As far as our nation is concerned, the definition of security industry is "an industry offering protection for human bodies, important infrastructure, information, financial system, as well as offering equipment to defend the security of national lands and the service"1 as initially defined by "Security Industry Program Office." Judging from the illustration of the definition, the security industry should be inter-disciplinary and integrative, which covers almost all walks of life and fields, such as high-tech industrial security management, traffic & transportation security management, fire control and prevention against natural calamities, disaster relief, information security management, security management in defense of national borders, and prevention of epidemics. After the staged mission, "e-Taiwan program", was accomplished in 2007, our government hoped to construct a good surrounding by creating a comfortable life from a user’s point-of-view. This was hoped to be achieved by using "the development of a high-quality internet society" as a main source by using innovative services, internet convergence, perceptive environment, security, trust, and human machine linkage. At the Economic Development Vision for 2015: First-Stage Three-Year Sprint Program (2007~2009) formulated by the Executive Yuan, wireless broadband, CPU computer-controlled items all have become part of our every day lives, and healthcare, along with the green industry are listed as the next emerging industries; whereby the development of relevant critical technologies is hoped to be promoted to create higher industrial values and commercial opportunities. However, from a digitally-controlled-life viewpoint, the issue concerned by all walks of life is no longer confined to the convenience and security of personal life but gradually turns to protection of security of a critical infrastructure (CI) run by using information technology. For instance, finance management, stock market, communication network, harbors and airports, high speed rail, R&D of important technology, science parks, water purification facilities, water supply facilities, power, and energy facilities. 2Because security involves resources related with people's most fundamental living needs and is the most elementary economic activity of the society, it is regarded as an important core objective to promote the modern social security system. Therefore, critical infrastructure protection requires more dependence on information and communication technology to maintain the stability of finance and communication, as well as the security of facilities related with supply and economy of all sorts of livelihoods in order to ensure regular operation. With the influence of information and communication technology on the application of critical infrastructure on the increase, the society has increasingly deepened its dependence on the security of our cyber world. The concept and connotation of information security also keep extending with it toward the aforementioned critical infrastructure protection planning, making critical information infrastructure protection (CIIP) and critical infrastructure protection (CIP) more inseparable in concept3 , and becomes an important goal of policy implementation to achieve the vision of a digital lifestyle which is secure for every nation. In recent years, considerable resources have been invested to complete an environment whereby a legal system of “smart lifestyle” is developed. However, what has been done for infrastructure protection continues to appear as not being comprehensive enough. This includes vague definitions, scattered regulations and policies, different protection measures taken by different authorities in charge, obvious differences in relevant risk management measures and in the magnitude of management planning of information security and so on. These problems all influence the formation of national policies and are the obstacles to the promotion of relevant industrial development. In view of this, the 2008/2009 International CIIP Handbook will be used as the cornerstone of research in this project. After the discussion on how critical infrastructure protection is done in America, Germany and Japan, the contents of norms of regulations and policies regarding critical infrastructure protection in our nation will be explored to make an in-depth analysis on the advantages and disadvantages of relevant norms. It is hoped to find out what is missing or omitted in the regulations and policies of our nation and to make relevant amendments. Suggestions will also be proposed so that the construction of a safe environment whereby the digital age of our nation can be expanded to assist the “smart lifestyle” to be developed further. 1.See http://tsii.org.tw/modules/tinyd0/index.php?id=14 (last visited May 24, 2009) 2.For "2008 International Conference on Homeland Security and Application of Technology in Taiwan ~ Critical Infrastructure Protection~", please visit http://www.tier.org.tw/cooperation/20081210.asp (last visit date: 05/17/2009). 3.For critical infrastructure protection, every nation has not only proceeded planning for physical facilities but put even more emphasis on protection jobs of critical information & communication infrastructure maintained via the information & communication technology. In the usage of relevant technical terms, the term "critical infrastructure" has also gradually been used to include the term "critical information & communication infrastructure". Elgin M. Brunner, Manuel Suter, Andreas Wenger, Victor Mauer, Myriam Dunn Cavelty, International CIIP Handbook 2008/2009, Center for Security Studies, ETH Zurich, 2008. 09, p. 37.
- Impact of Government Organizational Reform to Scientific Research Legal System and Response Thereto (1) – For Example, The Finnish Innovation Fund (“SITRA”)
- The Demand of Intellectual Property Management for Taiwanese Enterprises
- Blockchain in Intellectual Property Protection
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System
- Recent Federal Decisions and Emerging Trends in U.S. Defend Trade Secrets Act Litigation
- The effective and innovative way to use the spectrum: focus on the development of the "interleaved/white space"
- Copyright Ownership for Outputs by Artificial Intelligence
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System

