Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System

3.Commission of Technology and Innovation (CTI)
The CTI is also an institution dedicated to boosting innovation in Switzerland. Established in 1943, it was known as the Commission for the Promotion of Scientific Research[1]. It was initially established for the purpose of boosting economy and raising the employment rate, and renamed after 1996. The CTI and SNSF are two major entities dedicated to funding scientific research in Switzerland, and the difference between both resides in that the CTI is dedicated to funding R&D of the application technology and industrial technology helpful to Switzerland’s economic development.
Upon enforcement of the amended RIPA 2011, the CTI was officially independent from the Federal Office for Professional Education and Technology (OEPT) and became an independent entity entitled to making decisions and subordinated to the Federal Department of Economic Affairs (FDEA) directly[2]. The CTI is subject to the council system, consisting of 65 professional members delegated from industrial, academic and research sectors. The members assume the office as a part time job. CTI members are entitled to making decisions on funding, utilization of resources and granting of CTI Start-up Label independently[3].
The CTI primarily carries out the mission including promotion of R&D of industrial technology, enhancement of the market-orientation innovation process and delivery of R&D energy into the market to boost industrial innovation. For innovation, the CTI's core mission is categorized into[4]:
(1)Funding technology R&D activities with market potential
The CTI invests considerable funds and resources in boosting the R&D of application technology and industrial technology. The CTI R&D Project is intended to fund private enterprises (particularly small-sized and medium-sized enterprises) to engage in R&D of innovation technology or product. The enterprises may propose their innovative ideas freely, and the CTI will decide whether the funds should be granted after assessing whether the ideas are innovative and potentially marketable[5].
CTI’s funding is conditioned on the industrial and academic cooperation. Therefore, the enterprises must work with at least one research institution (including a university, university of science and technology, or ETH) in the R&D. Considering that small-sized and medium-sized enterprises usually do not own enough working funds, technology and human resources to commercialize creative ideas, the CTI R&D Project is intended to resolve the problem about insufficient R&D energy and funds of small- and medium-sized enterprises by delivering the research institutions’ plentiful research energy and granting the private enterprises which work with research institutions (including university, university of science and technology, or ETH) the fund. Notably, CTI’s funding is applicable to R&D expenses only, e.g., research personnel’s salary and expenditure in equipment & materials, and allocated to the research institutions directly. Meanwhile, in order to enhance private enterprises' launch into R&D projects and make them liable for the R&D success or failure, CTI’s funding will be no more than 50% of the total R&D budget and, therefore, the enterprises are entitled to a high degree of control right in the process of R&D.
The industrial types which the CTI R&D Project may apply to are not limited. Any innovative ideas with commercial potential may be proposed. For the time being, the key areas funded by CTI include the life science, engineering science, Nano technology and enabling sciences, etc.[6] It intends to keep Switzerland in the lead in these areas. As of 2011, in order to mitigate the impact of drastic CHF revaluation to the industries, the CTI launched its new R&D project, the CTI Voucher[7]. Given this, the CTI is not only an entity dedicated to funding but also plays an intermediary role in the industrial and academic sectors. Enterprises may submit proposals before finding any academic research institution partner. Upon preliminary examination of the proposals, the CTI will introduce competent academic research institutions to work with the enterprises in R&D, subject to the enterprises' R&D needs. After the cooperative partner is confirmed, CTI will grant the fund amounting to no more than CHF3,500,000 per application[8], provided that the funding shall be no more than 50% of the R&D project expenditure.
The CTI R&D Project not only boosts innovation but also raises private enterprises’ willingness to participate in the academic and industrial cooperation, thereby narrowing the gap between the supply & demand of innovation R&D in the industrial and academic sectors. Notably, the Project has achieved remarkable effect in driving private enterprises’ investment in technology R&D. According to statistical data, in 2011, the CTI solicited additional investment of CHF1.3 from a private enterprise by investing each CHF1[9]. This is also one of the important reasons why the Swiss innovation system always acts vigorously.
Table 1 2005-2011 Passing rate of application for R&D funding
|
Year |
2011 |
2010 |
2009 |
2008 |
2007 |
2006 |
2005 |
|
Quantity of applications |
590 |
780 |
637 |
444 |
493 |
407 |
522 |
|
Quantity of funded applications |
293 |
343 |
319 |
250 |
277 |
227 |
251 |
|
Pass rate |
56% |
44% |
50% |
56% |
56% |
56% |
48% |
Data source: Prepared by the Study
(2)Guiding high-tech start-up
Switzerland has learnt that high-tech start-ups are critical to the creation of high-quality employment and boosting of economic growth, and start-ups were able to commercialize the R&D results. Therefore, as of 2001, Switzerland successively launched the CTI Entrepreneurship and CTI Startup to promote entrepreneurship and cultivate high-tech start-ups.
1.CTI Entrepreneurship
The CTI Entrepreneurship was primarily implemented by the Venture Lab founded by CTI investment. The Venture Lab launched a series of entrepreneurship promotion and training courses, covering day workshops, five-day entrepreneurship intensive courses, and entrepreneurship courses available in universities. Each training course was reviewed by experts, and the experts would provide positive advice to attendants about innovative ideas and business models.
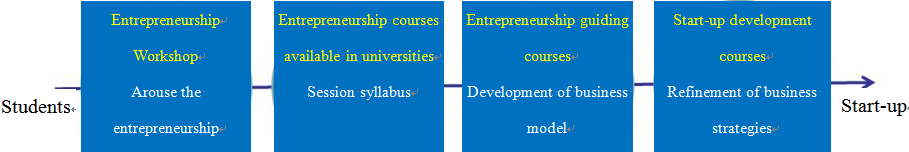
Data source: Venture Lab Site
Fig. 3 Venture Lab Startup Program
2.CTI Startup
The CTI is dedicated to driving the economy by virtue of innovation as its priority mission. In order to cultivate the domestic start-ups with high growth potential in Switzerland, the CTI Startup project was launched in 1996[10] in order to provide entrepreneurs with the relevant guidance services. The project selected young entrepreneurs who provided innovative ideas, and guided them in the process of business start to work their innovative ideas and incorporate competitive start-ups.
In order to enable the funding and resources to be utilized effectively, the CTI Startup project enrolled entrepreneurs under very strict procedure, which may be categorized into four stages[11]:
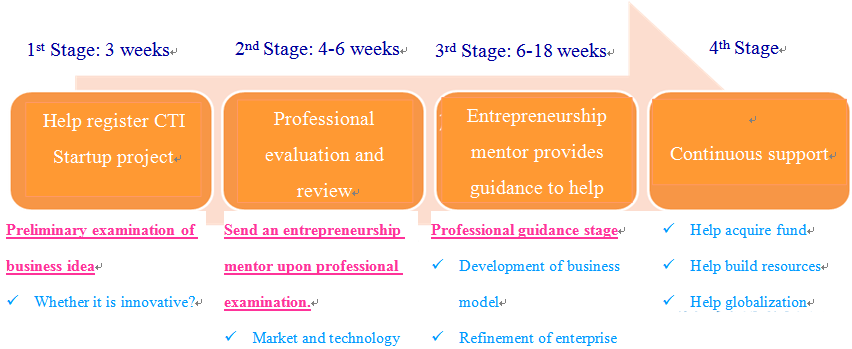
Data source: CTI Startup Site
Fig. 4 Startup Plan Flow Chart
In the first stage, the CTI would preliminarily examine whether the applicant’s idea was innovative and whether it was technologically feasible, and help the applicant register with the CTI Startup project. Upon registration, a more concrete professional examination would be conducted at the second stage. The scope of examination included the technology, market, feasibility and management team’s competence. After that, at the stage of professional guidance, each team would be assigned a professional “entrepreneurship mentor”, who would help the team develop further and optimize the enterprise’s strategy, flow and business model in the process of business start, and provide guidance and advice on the concrete business issues encountered by the start-up. The stage of professional guidance was intended to guide start-ups to acquire the CTI Startup Label, as the CTI Startup Label was granted subject to very strict examination procedure. For example, in 2012, the CTI Startup project accepted 78 applications for entrepreneurship guidance, but finally the CTI Startup Label was granted to 27 applications only[12]. Since 1996, a total of 296 start-ups have acquired the CTI Startup Label, and more than 86% thereof are still operating now[13]. Apparently, the CTI Startup Label represents the certification for innovation and on-going development competence; therefore, it is more favored by investors at the stage of fund raising.
Table 2 Execution of start-up plans for the latest three years
|
|
Quantity of application |
Quantity of accepted application |
Quantity of CTI Label granted |
|
2012 |
177 |
78 |
27 |
|
2011 |
160 |
80 |
26 |
|
2010 |
141 |
61 |
24 |
Data source: CTI Annual Report, prepared by the Study
Meanwhile, the “CTI Invest” platform was established to help start-up raise funds at the very beginning to help commercialize R&D results and cross the valley in the process of R&D innovation. The platform is a private non-business-making organization, a high-tech start-up fund raising platform co-established by CTI and Swiss investors[14]. It is engaged in increasing exposure of the start-ups and contact with investors by organizing activities, in order to help the start-ups acquire investment funds.
(3)Facilitating transfer of knowledge and technology between the academic sector and industrial sector
KTT Support (Knowledge & Technology Transfer (KTT Support) is identified as another policy instrument dedicated to boosting innovation by the CTI. It is intended to facilitate the exchange of knowledge and technology between academic research institutions and private enterprises, in order to transfer and expand the innovation energy.
As of 2013, the CTI has launched a brand new KTT Support project targeting at small-sized and medium-sized enterprises. The new KTT Support project consisted of three factors, including National Thematic Networks (NTNs), Innovation Mentors, and Physical and web-based platforms. Upon the CTI’s strict evaluation and consideration, a total of 8 cooperative innovation subjects were identified in 2012, namely, carbon fiber composite materials, design idea innovation, surface innovation, food study, Swiss biotechnology, wood innovation, photonics and logistics network, etc.[15] One NTN would be established per subject. The CTI would fund these NTNs to support the establishment of liaison channels and cooperative relations between academic research institutions and industries and provide small- and medium-sized enterprises in Switzerland with more rapid and easy channel to access technologies to promote the exchange of knowledge and technology between both parties. Innovation Mentors were professionals retained by the CTI, primarily responsible for evaluating the small-sized and medium-sized enterprises’ need and chance for innovation R&D and helping the enterprises solicit competent academic research partners to engage in the transfer of technology. The third factor of KTT Support, Physical and web-based platforms, is intended to help academic research institutions and private enterprises establish physical liaison channels through organization of activities and installation of network communication platforms, to enable the information about knowledge and technology transfer to be more transparent and communicable widely.
In conclusion, the CTI has been dedicated to enhancing the link between scientific research and the industries and urging the industrial sector to involve and boost the R&D projects with market potential. The CTI’s business lines are all equipped with corresponding policy instruments to achieve the industrial-academic cooperation target and mitigate the gap between the industry and academic sectors in the innovation chain. The various CTI policy instruments may be applied in the following manner as identified in the following figure.
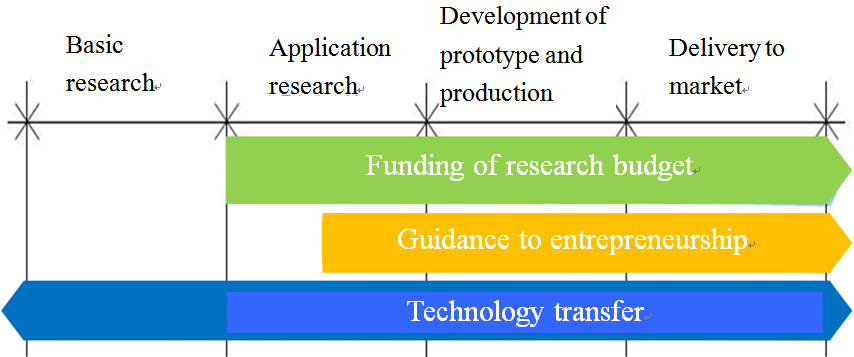
Data source: CTI Annual Report 2011
Fig. 5 Application of CTI Policy Instrument to Innovation Chain
III. Swiss Technology R&D Budget Management and Allocation
The Swiss Federal Government has invested considerable expenditures in technology R&D. According to statistic data provided by Swiss Federal Statistical Office (FSO) and OECD, the Swiss research expenditures accounted for 2.37% of the Federal Government’s total expenditures, following the U.S.A. and South Korea (see Fig. 6). Meanwhile, the research expenditures of the Swiss Government grew from CHF2.777 billion in 2000 to CHF4.639 billion in 2010, an average yearly growth rate of 5.9% (see Fig. 7). It is clear that Switzerland highly values its technology R&D.
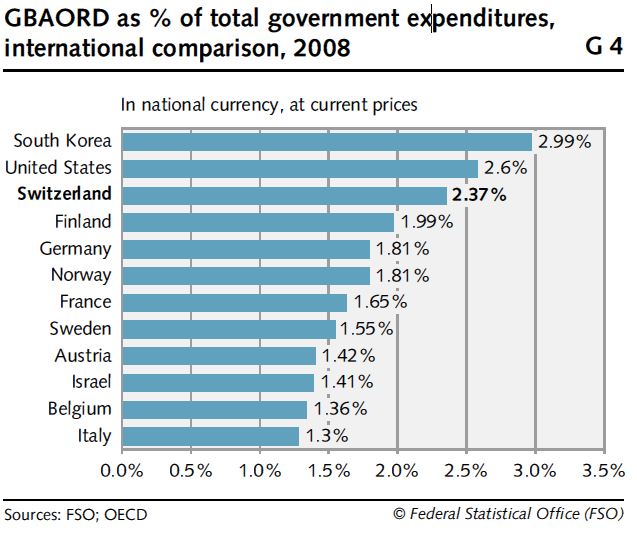.jpg)
Data source: FSO and OECD
Fig. 6 Percentage of Research Expenditures in Various Country Governments’ Total Expenditures (2008)
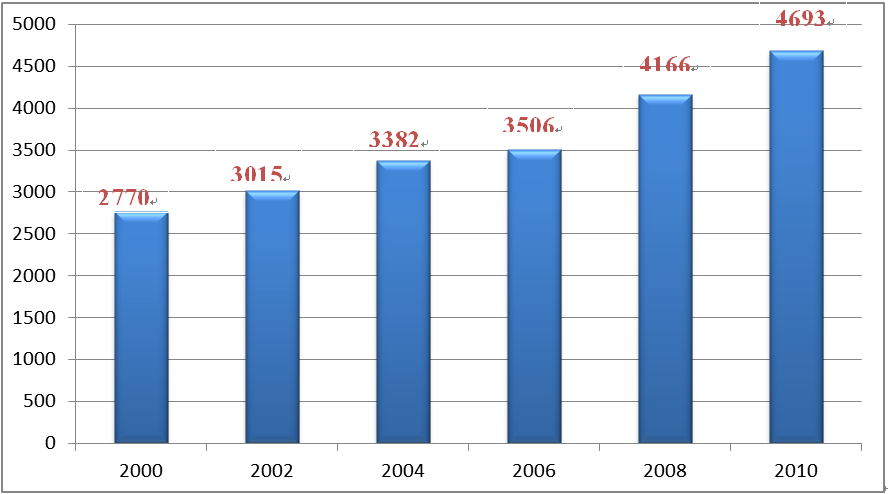
Data source: FSO and OECD
Fig. 7 Swiss Government Research Expenditures 2000-2010
1.Management of Swiss Technology R&D Budget
Swiss research expenditures are primarily allocated to the education, R&D and innovation areas, and play an important role in the Swiss innovation system. Therefore, a large part of the Swiss research expenditures are allocated to institutions of higher education, including ETH, universities, and UASs. The Swiss research expenditures are utilized by three hierarchies[16] (see Fig. 8):
- Government R&D funding agencies: The Swiss research budget is primarily executed by three agencies, including SERI, Federal Department of Economic Affairs, Education and Research, and Swiss Agency for Development and Cooperation (SDC).
- Intermediary R&D funding agencies: Including SNSC and CTI.
- Funding of R&D performing institutions: Including private enterprises, institutions of higher education and private non-profit-making business, et al.
Therefore, the Swiss Government research expenditures may be utilized by the Federal Government directly, or assigned to intermediary agencies, which will allocate the same to the R&D performing institutions. SERI will allocate the research expenditures to institutions of higher education and also hand a lot of the expenditures over to SNSF for consolidated funding to the basic science of R&D.
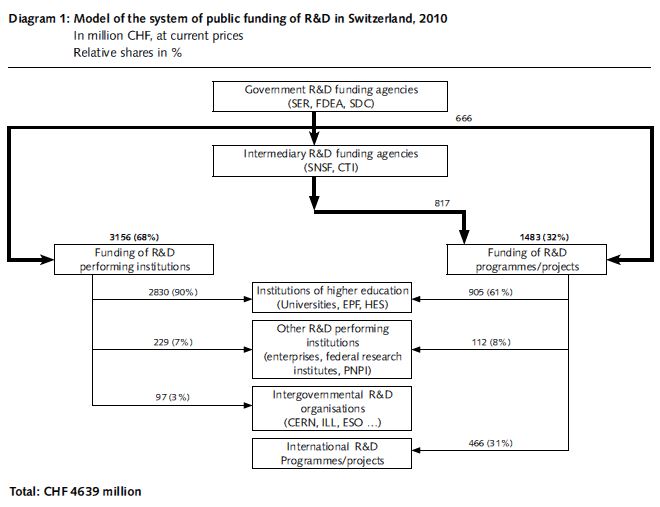
Data source: FSO
Fig. 8 Swiss Research Fund Utilization Mechanism
~to be continued~
[1] ORGANIZATION FOR ECONNOMIC CO-OPERATION AND DEVELOPMENT [OECD], OECD Reviews of Innovation Policy: Switzerland 27 (2006).
[2] As of January 1, 2013, the Federal Ministry of Economic Affairs was reorganized, and renamed into Federal Department of Economic Affairs, Education and Research (EAER).
[3] The Commission for Technology and Innovation CTI, THE COMMISSION FOR TECHOLOGY AND INNOVATION CTI, http://www.kti.admin.ch/org/00079/index.html?lang=en (last visited Jun. 3, 2013).
[4] Id.
[5] CTI INVEST, Swiss Venture Guide 2012 (2012), at 44, http://www.cti-invest.ch/getattachment/7f901c03-0fe6-43b5-be47-6d05b6b84133/Full-Version.aspx (last visited Jun. 4, 2013).
[6] CTI, CTI Activity Report 2012 14 (2013), available at http://www.kti.admin.ch/dokumentation/00077/index.html?lang=en&download=NHzLpZeg7t,lnp6I0NTU042l2Z6ln1ad1IZn4Z2qZpnO2Yuq2Z6gpJCDen16fmym162epYbg2c_JjKbNoKSn6A-- (last visited Jun. 3, 2013).
[7] CTI Voucher, THE COMMISSION FOR TECHOLOGY AND INNOVATION CTI, http://www.kti.admin.ch/projektfoerderung/00025/00135/index.html?lang=en (last visited Jun. 3, 2013).
[8] Id.
[9] CTI, CTI Activity Report 2011 20 (2012), available at http://www.kti.admin.ch/dokumentation/00077/index.html?lang=en&download=NHzLpZeg7t,lnp6I0NTU042l2Z6ln1ad1IZn4Z2qZpnO2Yuq2Z6gpJCDeYR,gWym162epYbg2c_JjKbNoKSn6A--(last visited Jun. 3, 2013).
[10] CTI Start-up Brings Science to Market, THE COMMISSION FOR TECHOLOGY AND INNOVATION CTI, http://www.ctistartup.ch/en/about/cti-start-/cti-start-up/ (last visited Jun. 5, 2013).
[11] Id.
[12] Supra note 8, at 45.
[13] Id.
[14] CTI Invest, http://www.cti-invest.ch/About/CTI-Invest.aspx (last visited Jun. 5, 2013).
[15] KTT Support, CTI, http://www.kti.admin.ch/netzwerke/index.html?lang=en (last visited Jun.5, 2013).
[16] Swiss Federal Statistics Office (SFO), Public Funding of Research in Switzerland 2000–2010 (2012), available at http://www.bfs.admin.ch/bfs/portal/en/index/themen/04/22/publ.Document.163273.pdf (last visited Jun. 20, 2013).
- Fig. 3 Venture Lab Startup Program [ png / 19 k ]
- Fig. 4 Startup Plan Flow Chart [ png / 28 k ]
- Fig. 5 Application of CTI Policy Instrument to Innovation Chain [ png / 40 k ]
- Fig. 6 Percentage of Research Expenditures in Various Country Governments’ Total Expenditures (2008) [ jpg / 68 k ]
- Fig. 7 Swiss Government Research Expenditures 2000-2010 [ png / 27 k ]
- Fig. 8 Swiss Research Fund Utilization Mechanism [ jpg / 50 k ]
Adopting Flexible Mechanism to Promote Public Procurement of Innovation—the Amendment of Article 27 of the Statute for Industrial Innovation I.Introduction To further industrial innovation, improve industrial environment, and enhance industrial competitiveness through a systematic long-term approach, the Statute for Industrial Innovation (hereinafter referred to as the Statute) has been formulated in Taiwan. The central government authority of this Statute is the Ministry of Economic Affairs, and the Industrial Development Bureau of the Ministry of Economic Affairs (henceforth referred to as the IDB) is the administrative body for the formulation of this Statute. Since its formulation and promulgation in 2010, the Statute has undergone four amendments. The latest amendment, passed by the Legislative Yuan on November 3, 2017, on the third reading, is a precipitate of the international industrial development trends. The government is actively encouraging the investment in industrial innovation through a combination of capital, R&D, advanced technologies and human resources to help the promotion of industrial transformation, hence this large scale amendment is conducted. The amendment, promulgated and enacted on November 22, 2017, focuses on eight key points, which include: state-owned businesses partaking in R&D (Article 9-1 of the amended provisions of the Statute), the tax concessions of the limited partnership venture capital businesses (Article 2, Article 10, Article 12-1 and Article 23-1 of the amended provisions of the Statute), the tax concessions of Angel Investors (Article 23-2 of the amended provisions of the Statute), applicable tax deferral of employees' stock compensation (Article 19-1 of the amended provisions of the Statute), tax deferral benefit of stocks given to research institution creators (Article 12-2 of the amended provisions of the Statute), the promotion of flexible mechanism for innovation procurement (Article 27 of the amended provisions of the Statute), the establishment of evaluation mechanism for intangible assets (Article 13 of the amended provisions of the Statute), and forced sale auction of idled land for industrial use (Article 46-1 of the amended provisions of the Statute). This paper focuses on the amendment of Article 27 of the Fourth Revision of the Statute, which is also one of the major focuses of this revision—promoting flexible mechanism for innovation procurement, using the mass-market purchasing power of the government as the energetic force for the development of industrial innovation. II.Explanation of the Amendment of Article 27 of the Statute 1.Purposes and Descriptions of the Amendment of Article 27 of the Statute The original intent of Article 27 (hereinafter referred to as the Article) of the Statute, prior to the latest amendment (content of the original provisions is shown in Table 1), was to encourage government agencies and enterprises to give a priority to using green products through the "priority procurement" provisions of Paragraph 2, which allow government agencies to award contracts to green product producers using special government procurement procedures, so as to increase the opportunities for government agencies to use green products, and thereby promote the sustainable development of the industry. In view of the inherent tasks of promoting the development of industrial innovation, and considering that, using the large-scale government procurement demand to guide industrial innovation activities, has become the policy instrument accepted by most advanced countries, the IDB expects that, with the latest amendment of Article 27, the procurement mechanism policy for software, innovative products and services, in addition to the original green products, may become influential, and that "innovative products and services" may be included in the scope of "Priority Procurement" of this Article namely, make “priority procurement of innovative products and services” as one of the flexible mechanisms for promoting innovation procurement. A comparison of the amended provisions and the original provisions is shown in Table 1, and an explanation of the amendment is described as follows:[1] Table 1 A Comparison of Article 27 Amendment of the Statute for Industrial Innovation Amended Provisions Original Provisions Article 27 (I) Each central government authority in charge of end enterprises of a specific industry shall encourage government organizations (agencies) and enterprises to procure software, innovative and green products or services. (II) To enhance the procurement efficiencies, as effected by supply and demand, the central government authority shall offer assistance and services to the organizations (agencies) that handle these procurements as described in the preceding paragraph; wherein, Inter-entity Supply Contracts that are required for the aforesaid procurements, the common requirements shall be decided, in accordance with policy requirements, upon consultation between the central government authority and each central government authority in charge of end enterprises of a specific industry. (III) Where the software, innovative and green products or services, as described in Paragraph 1, must be tested, audited, accredited and certified, their associated fees and charges may be reduced, exempted, or suspended. (IV) Government organizations (agencies) may specify in the tender document the priority procurement of innovative and green products or services that have been identified to meet the requirements of paragraph 1. However, such a specification shall not violate treaties or agreements that have been ratified by the Republic of China. The measures concerning specifications, categories, and identification procedures of software, innovative and green products or services as prescribed in Paragraph 1; the testing, auditing criteria, accreditation and certification as prescribed in paragraph 3; and the Priority Procurement in paragraph 4 and other relevant items, shall be established by each central government authority in charge of end-enterprises of a specific industry. Article 27 (I) Each central government authority in charge of end enterprises shall encourage government agencies and enterprises to give priority to green products that are energy/resources recyclable/renewable, energy and water saving, non-toxic, less-polluting, or able to reduce the burden on the environment. (II) Agencies may specify in the tender documents that priority is given to green products meeting the requirement set forth in the preceding Paragraph. (III) The regulations governing the specifications, categories, certification procedures, review standards, and other relevant matters relating to the green products as referred to in the preceding Paragraph shall be prescribed by the central government authorities in charge of end enterprises. Source: The Ministry of Economic Affairs (I).Paragraph 1 In order to compel each central government authority in charge of end enterprises of a specific industry to motivate industrial innovation activities and sustainable development on the basis of requirements, and to support the development of the software industry in Taiwan, the provision, that such an authority should encourage government organizations (agencies) and enterprises to procure software and innovative products and services, is added in paragraph 1. (II).Paragraph 2 This procurement, as described in paragraph 1, is different from the property or services procurement of general affairs as handled by various organizations. To enhance procurement efficiencies, as effected by supply and demand, the central government authority, i.e., the Ministry of Economic Affairs, shall provide relevant assistance and services to organizations (agencies) handling these procurements, hence the added provisions in paragraph 2. For purchases using inter-entity supply contracts, which are bound by the requirements of this Article, due to their prospective nature, and that the common demand of each organization is difficult to make an accurate estimate by using a demand survey or other method, the Ministry of Economic Affairs shall discuss the issues with each central government authority in charge of end-enterprises of a specific industry, who consult or promote policies, and are in charge of end enterprises of a specific industry, and then make decisions in accordance with the policy promotion requirements. (III).Paragraph 3 The fee schedule for testing, auditing, accrediting and certifying software, innovative and green products or services is covered by Article 7, Administrative Fees of the Charges And Fees Act. The authorities in charge should determine relevant fee standards.However, considering that the test, audit, accreditation and certification may be conducted during a trial or promotional period, or circumstances dictate that it is necessary to motivate tenderer participation, the fee may be reduced, waived or suspended; hence, paragraph 3 is added. (IV).Paragraph 4 Paragraph 2 of the original provision is moved to paragraph 4 with the revisions made to paragraph 1, accordingly, and the provision for using Priority Procurement to handle innovative products or services is added. However, for organizations covered by The Agreement on Government Procurement (GPA), due to Taiwan's accession to the WTO, ANZTEC, and ASTEP, their procurement of items covered in the aforesaid agreements with a value reaching the legislated threshold, shall be handled in accordance with the regulations stipulated in the aforesaid agreements; hence the stipulation in the proviso that the procurement must not violate the provisions of treaties or agreements ratified by the Taiwan government. (V).Paragraph 5 Paragraph 3 of the original Article is moved to paragraph 5 with the revisions made to paragraph 1, accordingly, and the provision, that authorizes each central government authority in charge of end enterprises of a specific industry to determine appropriate measures concerning the methods of defining software, innovative and green products and services, as well as matters relating to test, accreditation, certification and priority procurement, is added. 2.The Focus of the Amendment of Article 27 of the Statute—Promoting a Flexible Mechanism for Innovation Procurement As previously stated, the amendment of this Article aims to stimulate activities of industrial innovation by taking advantage of the huge demand from government agencies. With the government agencies being the users of the innovative products or services, government's procurement market potential is tapped to support the development of industrial innovation. The original intention of amendment is to incorporate the spirit of Public Procurement of Innovation[2] into this Article, and to try to introduce EU's innovation procurement mechanism[3] into our laws. So that, a procurement procedure, that is more flexible and not subject to the limitation of procurement procedures currently stipulated by the Government Procurement Act, may be adopted to facilitate government sector action in taking the lead on adopting innovative products or services that have just entered their commercial prototype stage, or utilizing the demand for innovation in the government sector to drive industry's innovative ideas or R&D (that can not be satisfied with the existing solutions in the marketplace). However, while it is assessing the relevant laws and regulations of our government procurement system and the practice of implementation, the use of the current government procurement mechanism by organizations in the public sector to achieve the targets of innovation procurement is still in its infancy. It is difficult to achieve the goal, in a short time, of establishing a variety of Public Procurement of Innovation Solutions (PPI Solutions) as disclosed in the EU's Directive 2014/24 / EU, enacted by the EU in 2014, in ways that are not subject to current government procurement legislation. Hence, the next best thing: Instead of setting up an innovative procurement mechanism in such a way that it is "not subject to the restrictions of the current government procurement law", we will focus on utilizing the flexible room available under the current system of government procurement laws and regulations, and promoting the "flexible mechanism for innovation procurement” paradigm. With the provisions now provided in Article 27 of the Statute for Industrial Innovation, the government sector is authorized to adopt the "Priority Procurement" method on innovative products and services, thus increasing the public sector's access to innovative products and services. With this amendment, in addition to the "green products" listed in the original provisions of paragraph 1 of the Statute, "software" and "innovative products or services"[4] are now incorporated into the target procurement scope and each central government authority in charge of end enterprises of a specific industry should now encourage government organizations and enterprises to implement; however, the provisions of this paragraph do not have the specific effect of law, they are declaratory provisions. Two priorities are the1 primary focus of the provisions of paragraph 2 and paragraph 4 of this Article for promoting flexible mechanism for innovation procurement: (I)The procurement of software, innovative and green products or services that uses Inter-entity Supply Contracts may rely on the "policy requirement" to establish the common demand. According to the first half of the provisions of paragraph 2 of this Article, the Ministry of Economic Affairs, being the central government authority of the Statute, may provide assistance and services to organizations dealing with the procurement of software, innovative and green products and services.This is because the procurement subjects, as pertaining to software, products or services that are innovative and green products (or services), usually have the particularities (especially in the software) of the information professions; different qualities (especially in innovative products or services), and are highly profession-specific. They are different from the general affairs goods and services procured by most government agencies. Hence, the Ministry of Economic Affairs may provide assistance and service to these procurement agencies, along with the coordination of relevant organizations, in matters relating to the aforesaid procurement process in order to improve procurement efficiency as relates to supply and demand. Pursuant to the second half of Paragraph 2 of this Article, if the inter-entity supply contract method is used to process the procurement of software, innovative products and services, green products (or services) and other related subjects, there could be "Commonly Required" by two or more organizations concerning the procurement subjects, so in accordance with the stipulations of Article 93 of the Government Procurement Act, and Article 2 of the Regulations for The Implementation of Inter-entity Supply Contracts[5], an investigation of common requirements should be conducted first. However, this type of subject is prospective and profession-specific (innovative products or services in particular), and government organizations are generally not sure whether they have demand or not, which makes it difficult to reliably estimate the demand via the traditional demand survey method[6], resulting in a major obstacle for the procurement process. Therefore, the provisions are now revised to allow the Ministry of Economic Affairs to discuss procurement with each central government authority in charge of end enterprises of a specific industry, who consult or promote policies (such as the National Development Council, or central government authority in charge of end enterprises of a specific industry relevant to the procurement subjects), and then make decisions based on the quantities of goods and services of common requirements in accordance with the demand for promoting the policy. The provisions explicitly stipulate such flexibility in adopting methods other than the "traditional demand survey" method, as is required by laws for the common demand of Inter-entity Supply Contracts. Thus, agencies currently handling procurement of prospective or innovative subjects using inter-entity supply contracts, may reduce the administrative burden typically associated with conducting their own procurement. In addition, with a larger purchase quantity demand, as generated from two or more organizations, the process can more effectively inject momentum into the industry, and achieve a win-win situation for both supply and demand. (II)Government organizations may adopt "Priority Procurement" when handling procurement of innovative and green products or services. Prior to the amendment, the original provision of paragraph 2 of this Article stipulates that organizations may specify in the tender document Priority Procurement of certified green products; Additionally, a provision of paragraph 3 of the original Article stipulates that each central government authority in charge of end enterprises of a specific industry is authorized to establish the specifications, categories and other relevant matters of the green products[7] (according to the interpretation of the original text, it should include "Priority Procurement" in paragraph 3 of the Article).After the amendment of the Article, paragraph 2 of the original Article is moved to paragraph 4. In addition to the original green products, "innovative products or services" are included in the scope of "Priority Procurement" that organizations are permitted to adopt (but, the "software" in paragraph 1 was not included[8]). However, for organizations covered by The Agreement on Government Procurement (GPA), due to Taiwan's accession to the WTO, ANZTEC, and ASTEP, their procurement of items covered by the aforesaid agreements with a value reaching the stated threshold, shall be handled in accordance with the regulations stipulated in the aforesaid agreements; hence the stipulation in the proviso that the procurement must not violate the provisions in treaties or agreements ratified by the Taiwan government. Additionally, paragraph 3 of the original Article is moved to paragraph 5. Each central government authority in charge of end enterprises of a specific industry is authorized to use their own judgment on matters concerning the specifications, categories, certification processes of software, innovative and green products or services and the method for Priority Procurement of paragraph 4. In accordance with the authorization in paragraph 5 of the amended provision of this Article, each central government authority in charge of end enterprises of a specific industry may, depending on the specific policy requirement that promotes innovation development of its supervised industry, establish methods of identification and the processes of Priority Procurement for “Specific categories of innovative products or services", especially on products or services fitting the requirements of the method of using the demands of government organizations to stimulate industrial innovation. The established "Regolations for priority procurement of Specific categories of innovative products or services" is essentially a special regulation of the government procurement legislation, which belongs to the level of regulations, that is, it allows the organizations to apply measures other than the government procurement regulations and its related measures to the procurement process, and adopt "Preferential Contract Awarding" for qualified innovative products or services. Any government agency that has the need to procure a particular category of innovative product or service may, in accordance with the provisions of paragraph 4 of this Article, specify the use of Priority Procurement in the tender document, and administer the procurement, in accordance with the process of this particular category of innovative products, or priority procurement. The agency is now enabled to follow a more flexible procurement process than that of the government procurement regulations to more smoothly award contracts for qualified innovative products or services. Citing two examples of this applied scenario: Example one, "innovative information services": The central government authority in charge of information services is IDB. Thus, IDB may, according to the authorization provided for in paragraph 5 of the Article, establish the identification methods for innovative information services (the purpose of which is to define the categories and specifications of innovative services covered in the scope of priority procurement) and priority procurement processes, pertaining to emerging information services that are more applicable to the requirements of government agencies, such as: cloud computing services, IoT services, and Big Data analysis services.Example two, "Innovative construction or engineering methods": The central government authority in charge of construction affairs is the Construction and Planning Agency of the Ministry of the Interior. Since the agency has already established the "Guidelines for Approval of Applications for New Construction Techniques, Methods, Equipment and Materials", the agency may establish a priority procurement process for new construction techniques, methods or equipment, in accordance with the stipulations in paragraph 5 of the Article. Government agencies may conduct procurement following any of these priority procurement practices, if there is a requirement for innovative information services, or new construction techniques, methods or equipment. In addition to the two aforementioned flexible mechanisms for innovation procurement, where government agencies are granted flexible procedures to handle the procurement of innovative products or services via the use of the flexible procurement mechanism, paragraph 3, concerning the incentive measures of concessionary deductions, is added to the Article to reduce the bidding costs for tenderers participating in the tender. For the Procurement of software, innovative and green products or services encouraged by each central government authority in charge of end-enterprises of a specific industry (not limited to those handled by the authorities themselves, using inter-entity supply contracts or priority procurement methods), if the procurement subjects are still required to be tested, audited, accredited and certified by the government agencies, such a process falls under the scope of administrative fees collection, pursuant to paragraph 1 Article 7 of the Charges And Fees Act. However, considering that the item subject to test, audit, accreditation and certification may be in a trial or promotional period, or that it may be necessary to motivate tenderer participation, the provisions of paragraph 3 are thusly added to the Article to reduce, waive, or suspend the collection of aforementioned fees. Executive authorities in charge of collecting administrative fees shall proceed to reduce, waive, or suspend the collection pursuant to the stipulations of paragraph 3 of the Article and Article 12 subparagraph 7 of the Charges And Fees Act.[9] III.The direction of devising supporting measures of flexible mechanism for innovation procurement The latest amendment of the Statute for Industrial Innovation was promulgated and enacted on November 22, 2017, it is imperative that supporting measures pertaining to Article 27 of the Statute be formulated. As previously stated, the flexible mechanism for innovation procurement, as promoted in this Article, is designed specifically for the products or services that are pertinent to the government procurement requirements and are capable of stimulating industrial innovation, and providing a more flexible government procurement procedure for central authorities in charge of a specific industry as a policy approach in supporting industry innovation. Thus, the premise of devising relevant supporting measures is dependent on whether the specific industry, as overseen by the particular central authority, has a policy in place for promoting the development of industrial innovation, and on whether it is suitable in promoting the flexible mechanism for innovation procurement as described in this Article. The purpose of this Article is to promote the flexible mechanism for innovation procurement. Supporting measures pertaining to this Article will focus on the promotion of devising an "Innovation Identification Method", and of the "Priority Procurement Process" of the innovative products or services of each industry that central government authorities oversee. The former will rely on each central government authority in charge of a specific industry to charter an industry-appropriate and profession-specific planning scheme; while, for the latter, the designing of a priority procurement process, in accordance with the nature of the various types of innovative products or services, does not have to be applicable to all. However, regardless what type of innovative products or services the priority procurement process is designed for, the general direction of consideration should be given to - taking the different qualities of innovative products or services as the core consideration. Additionally, the attribute of the priority procurement procedures focusing specifically on the different qualities of the innovative subjects relates to the special regulation relevant to the government procurement regulations. Thus, the procurement procedures should follow the principle that if no applicable stipulation is found in the special regulation, the provisions of the principal regulation shall apply. The so-called "Priority Procurement" process refers to the "Preferential Contract Awarding" on tenders that meet certain criteria in a government procurement procedure. The existing Government Procurement Act (GPA, for short) and its related laws that have specific stipulations on "Priority Procurement" can be found in the "Regulations for Priority Procurement of Eco-Products" (Regulations for Eco-Products Procurement, for short), and the "Regulations for Obliged Purchasing Units / Institutions to Purchase the Products and Services Provided by Disabled Welfare Institutions, Organizations or Sheltered Workshops" (Regulations for Priority Procurement of Products or Services for Disabled or Shelters, for short). After studying these two measures, the priority procurement procedures applicable to criteria-conformed subjects can be summarized into the following two types: 1.The first type: Giving preferential contract awarding to the tenderer who qualifies with "the lowest tender price”, as proposed in the tender document, and who meets a certain criteria (for example, tenderers of environmental products, disabled welfare institutions, or sheltered workshops). There are two scenarios: When a general tenderer and the criteria-conformed tenderer both submit the lowest tender price, the criteria-conformed tenderer shall obtain the right to be the "preferential winning tender" without having to go through the Price Comparison and Reduction Procedures. Additionally, if the lowest tender price is submitted by a general tenderer, then the criteria-conformed tenderers have the right to a "preferential price reduction” option, that is, the criteria-conformed tenderers can be contacted, in ascending order of the tender submitted, with a one time option to reduce their bidding prices. The first tenderer who reduces their price to the lowest amount shall win the tender. Both the Regulations for Eco-Products Procurement[10] and Regulations for Priority Procurement of Products or Services for Disabilities or Shelters[11] have such relevant stipulations. 2.The second type: It is permitted to give Preferential Contract Awarding to a criteria-conformed tenderer, when the submitted tender is within the rate of price preference. When the lowest tenderer is a general tenderer, and the tender submitted by the criteria-conformed tenderer is higher than the lowest tender price, the law permits that if the tender submitted is "within the rate of price preference ", as set by the procuring entity, the procuring entity may award the contract preferentially to "the tender submitted by the criteria-conformed tenderer." The premise for allowing this method is that the tender submitted by the criteria-conformed tenderer must be within the preferential price ratio. If the submitted tender is higher than the preferential price ratio, then the criteria-conformed tenderer does not have the right to preferential contract awarding. The contract will be awarded to theother criteria-conformed tenderer, or to a general tenderer. This method is covered in the provisions of the Regulations for Eco-Products Procurement[12]. However, the important premise for the above two priority procurement methods is that the nature of the subject matter of the tender is suitable for adopting the awarding principle of the lowest tender (Article 52, Paragraph 1, Subparagraphs 1 and 2 of the Procurement Act), that is, it is difficult to apply these methods to the subjects if they are different qualities. Pursuant to the provisions of Article 66 of the Enforcement Rules of the Government Procurement Act, the so-called "different qualities" refers to the construction work, property or services provided by different suppliers that are different in technology, quality, function, performance, characteristics, commercial terms, etc. Subjects of different qualities are essentially difficult to compare when based on the same specifications. If just looking at pricing alone it is difficult to identify the advantages and disadvantages of the subjects, hence, the awarding principle of the lowest tender is not appropriate. The innovative subjects are essentially subjects of different qualities, and under the same consideration, they are not suitable for applying the awarding principle of the lowest tender. Therefore, it is difficult to adopt the lowest-tender-based priority procurement method for the procurement of innovative subjects. In the case of innovative subjects with different qualities, the principle of the most advantageous tender should be adopted (Article 52 Paragraph 1 Subparagraph 3 of the Procurement Act) to identify the most qualified vender of the subjects through open selection. Therefore, the procedure for the priority procurement of innovative subjects with different qualities should be based on the most advantageous tender principle with focus on the "innovativeness" of the subjects, and consideration on how to give priority to tenderers, who qualify with the criteria of innovation. Pursuant to the provisions of Article 56 Paragraph 4 of the Procurement Act, the Procurement and Public Construction Commission has established the "Regulations for Evaluation of the Most Advantageous Tender". The tendering authorities adopting the most advantageous tender principle should abide by the evaluation method and procedures delineated in the method, and conduct an open selection of a winning tender. According to the Regulations for Evaluation of the Most Advantageous Tender, in addition to pricing, the tenderers' technology, quality, function, management, commercial terms, past performance of contract fulfillment, financial planning, and other matters pertaining to procurement functions or effectiveness, maybe chosen as evaluation criteria and sub-criteria. According to the three evaluation methods delineated in the provisions of Article 11 of the Regulations for Evaluation of the Most Advantageous Tender (overall evaluation score method, price per score point method, and ranking method), pricing could not been included in the scoring. That is, "the prices of the subjects" is not the absolute criterion of evaluation of the most advantageous tender process. The priority procurement procedures designed specifically for innovative subjects with different qualities may adopt an evaluation method that excludes "pricing" as part of the scoring criterion so as to give innovative subject tenderers the opportunity to be more competitive in the bidding evaluation process, and due to the extent of their innovativeness, obtain the right to preferential tenders. If it must be included in the scoring, the percentage of the total score for pricing should be reduced from its usual ratio[13], while stipulating explicitly that "innovation" must be included as part of the evaluation criteria. In addition, its weight distribution should not be less than a ratio that highlights the importance of innovation in the evaluation criteria. Furthermore, when determining how to give preference to tenderers who meet certain innovation criteria in the contract awarding procedures, care should be taken to stay on focus with the degree of innovation of the subject (the higher the degree of innovation, the higher the priority), rather than giving priority to arbitrary standards. In summary, with consideration of priority procurement procedures designed specifically for innovative subjects with different qualities, this paper proposes the following preliminary regulatory directions: 1.Adopt the awarding principle of the most advantageous tender. 2.Explicitly stipulate the inclusion of "innovation" in the evaluation criteria and sub-criteria, and its ratio, one that indicates its importance, should not be less than a certain percentage of the total score (for example 20%). 3.Reduce the distributed ratio of "price" in the scoring criteria in the open selection. 4.After the members of the evaluation committee have concluded the scoring, if more than two tenderers have attained the same highest overall evaluated score or lowest quotient of price divided by overall evaluated score, or more than two tenderers have attained the first ranking, the contract is awarded preferentially to the tenderer who scores the highest in the "innovation" criterion. 5.When multiple awards (according to Article 52 Paragraph 1 Subparagraph 4 of the Procurement Act) are adopted, that is, there is more than one final winning tender, the procuring entity may select the tenderers with higher innovation scores as the price negotiation targets for contract awarding, when there are more than two tenderers with the same ranking. Using the above method to highlight the value of innovative subjects will make these suppliers more competitive, because of their innovativeness ratings in the procurement procedures, and not confine them to the limitation of price-determination. So that, subject suppliers with a high degree of innovation, may attain the right to the preferential contract awarding that they deserve due to their innovativeness, and the procuring entity can purchase suitable innovative products in a more efficient and easy process. It also lowers the threshold for tenderers with innovation energy to enter the government procurement market, thus achieving the goal of supporting industrial innovation and creating a win-win scenario for supply and demand. [1] Cross-reference Table of Amended Provisions of the Statute for Industrial Innovation, The Ministry of Economic Affairs, https://www.moea.gov.tw/MNS/populace/news/wHandNews_File.ashx?file_id=59099 (Last viewed date: 12/08/2017). [2] According to the Guidance for public authorities on Public Procurement of Innovation issued by the Procurement of Innovation Platform in 2015, the so-called innovation procurement in essence refers to that the public sector can obtain innovative products, services, or work by using the government procurement processes, or that the public sector can administer government procurement with a new-and-better process. Either way, the implementation of innovation procurement philosophy is an important link between government procurement, R & D and innovation, which shortens the distance between the foresighted emerging technologies/processes and the public sector/users. [3] The EU's innovative procurement mechanism comprises the "Public Procurement of Innovation Solutions" (PPI Solutions) and "Pre-Commercial Procurement" (PCP). The former is one of the government procurement procedures, explicitly regulated in the new EU Public Procurement Directive (Directive 2014/24 / EU), for procuring solutions that are innovative, near or in preliminary commercial prototype; The latter is a procurement process designed to assist the public sector in obtaining technological innovative solutions that are not yet in commercial prototype, must undergo research and development process, and are not within the scope of EU Public Procurement Directive. [4] The "software, innovative and green products or services", as described in paragraph 1 of Article 27 of the amended Statute for Industrial Innovation, refers to, respectively, "software", "innovative products or services", and "green products or services" in general. There is no co-ordination or subordination relationship between the three; the same applies to "innovative and green products or services" in paragraph 4. [5] Article 93 of the Government Procurement Act stipulates: "An entity may execute an inter-entity supply contract with a supplier for the supply of property or services that are commonly needed by entities." Additionally, Article 2 of the Regulations for The Implementation of Inter-entity Supply Contracts stipulates: "The term 'property or services that are commonly needed by entities' referred to in Article 93 of the Act means property or services which are commonly required by two or more entities. The term 'inter-entity supply contract (hereinafter referred to as the “Contract”)' referred to in Article 93 of the Act means that an entity, on behalf of two or more entities, signs a contract with a supplier for property or services that are commonly needed by entities, so that the entity and other entities to which the Contract applies can utilize the Contract to conduct procurements." Therefore, according to the interpretation made by the Public Construction Commission, the Executive Yuan (PCC, for short), organizations handling inter-entity supply contracts should first conduct a demand investigation. [6] In general, organizations in charge of handling the inter-entity supply contracts will disseminate official documents to applicable organizations with an invitation to furnish information online about their interests and estimated requirement (for budget estimation) at government's e-procurement website. However, in the case of more prospective subjects (such as cloud services of the emerging industry), it may be difficult for an organization to accurately estimate the demand when filling out the survey, resulting in a mismatch of data between the demand survey and actual needs. [7] In accordance with the authorization of paragraph 3 of the Article, the IDB has established "Regulations Governing Examination and Identification of Advanced Recycled Products by Ministry of Economic Affairs" (including an appendix: Identification Specification for Resource Regenerating Green Products), except that the priority procurement process was not stipulated, because the Resource Regenerating Green Products, that meet the requirements of the Ministry of Economic Affairs, are covered by the "Category III Products" in the provisions of Article 6 of the existing "Regulations for Priority Procurement of Eco-Products", set forth by the PPC and The Environmental Protection Administration of the Executive Yuan. Hence, organizations that have the requirement to procure green products, may proceed with priority procurement by following the regulations in the "Regulations for Priority Procurement of Eco-Products". [8] After the amendment of the Article, the "software" in the provisions of paragraph 1 was excluded in paragraph 4, because the objective of paragraph 4 is to promote industry innovation and sustainable development with the use of a more flexible government procurement procedure. Thus, the subjects of the priority procurement mechanism are focused on "innovative" and "green" products or services, which exclude popular "software" that has a common standard in the market. However, if it is an "innovative software", it may be included in the "innovative products or services" in the provisions of paragraph 4. [9] According to the provisions of Article 12 of the Charges And Fees Act: "In any of the following cases, the executive authority in charge of the concerned matters may waive or reduce the amount of the charges and fees, or suspend the collection of the charges and fees: 7. Waiver, reduction, or suspension made under other applicable laws." [10] Refer to Article 12, Paragraph 1, Subparagraphs 1 and Article 13, Paragraph 1 and 2 of Regulations for Priority Procurement of Eco-Products. [11] Refer to Article 4 of Regulations for Obliged Purchasing Units / Institutions to Purchase the Products and Services Provided by Disabled Welfare Institutions, Organizations or Sheltered Workshops. [12] Refer to Article 12, Paragraph 1, Subparagraphs 2 and Article 13, Paragraph 3 of Regulations for Priority Procurement of Eco-Products. [13] The provisions of paragraph 3 Article 16 of the Regulations for Evaluation of the Most Advantageous Tender stipulates: Where price is included in scoring, its proportion of the overall score shall be not less than 20% and not more than 50%.
The Status of Taiwan's Regulations Concerning with Access to Biological ResourcesPreface In actual practice, the research and development of biotech medicine, food, and environmental products cannot be done by in-lab researches. This is a unique character of the biotechnology industry. To get the research going, the researchers need to search for and exploit new biological materials and, samples outside the lab. Therefore, the access to and management of biological resources have significant impact on the stimulation and development of national biotech industry. Ever since the enforcement of Convention on Biological Diversity (CBD) in 1992 by 172 countries, a general principal about conserving biological diversity and using biological resources has been set. According to CBD, States have sovereign rights over their own biological resources. CBD also encourages each State to access to and manage the biological resources conformed with the principals of conservation, sustainability, NOEL environment friendly, and adequate sharing of benefit arising from biological resources. Therefore, issues such as environmental protection and sustainability have become political issues internationally. If the ABS system for the access to biological resources is designed too strictly, the establishment of the system will make the research and development staffs and related institutions hang back with hesitation both domestically and internationally. Their intention of bioprospecting in the designated country will then be reduced. On the other hand, if the system is designed too loosely, it will not be able to protect the rights of the owner of the resources. As a result, currently, every country holds a cautious attitude in setting up the regulations of managing the access to biological resources. Currently, many countries and regional international organizations already set up ABS system, such as Andean Community, African Union, Association of Southeast Asia Nations (ASEAN), Australia, South Africa, and India, all are enthusiastic with the establishment of the regulations regarding the access management of biological resources and genetic resources. On the other hand, there are still many countries only use traditional and existing conservation-related regulations to manage the access of biological resources. Since it has been more than 10 years that the regulation of access to biological resources and benefit sharing has been developed in some countries, how is Taiwan's current situation regarding this issue? Taiwan's Existing Regulations on the Access to Bioloical Resources In terms of regulations, Taiwan's existing management style of the access to biological resources is similar to that of the US and the EU. It refers to the existing regulations on environmental protection and conservation, and evaluates from the perspective of environmental protection to control and manage the exploitation and application of the related biological resources. These regulations include the Wildlife Conservation Act, theNational Park Law, the Forestry Act, the Cultural Heritage Preservation Act, and the Aboriginal Basic Act. The paragraphs below describe the contents of the acts mentioned that are related to the access to biological resources. 1 、 Wildlife Conservation Act According to the Wildlife Conservation Act, the Protected Species and the products made of cannot be hunted, traded, owned, imported, exported, raised, bred, and processed unless the number of protected wildlife has exceeded the amount the environment permits, or carry the objectives of academic research and education with the permits of central or regional authorities. As for the hunting of General Wildlife, pre-application and approval is needed with the exception of projects based on the objectives of academic research or education. In addition, the import and export of the living wildlife and the products of Protected Wildlife are restricted to the condition of being permitted by management authority. With respect to the import and export of living Protected Wildlife, Academic research institutions and colleagues are the only person who can seek for the approval of management authority before they proceed. 2 、 National Park Law The design and management of Taiwan's national parks are based on the regulations listed in the National Park Law with the purpose of protecting our country's exclusive natural scenery, wildlife and historical spots. Based on the properties and the nature of resources, the national park management structures the preserved area into general control area, playground and resting area, spot of historical interest, special landmark area, and ecological protection area. Ecological protection area refers to the areas where the natural surroundings, creatures, the society they live and propagate are strictly protected only for the research of ecology. According to the regulation of National Park Law, inside the national park area, it is prohibited to hunt animals, fish, take off flowers or trees, not to mention the behaviours that are prohibited by the management authority. Exceptions are made based on the conditions of preserved areas and for the research purposes. In the general control area or resting area, the national park authority allows fishing or other activities agreed by the authority. However, these activities are prohibited in the preserved area of historical interest, special landmark area, and ecological protection area. To suit special purposes, in the special landmark area or ecological protection area, collection of specimens is allowed subject to the approval of authority. Under the purpose of academic research, better management of public safety, and special management of national park, the Ministry of the Interior will permit the collection of specimen. However, to enter the ecological protection area, one must obtain the permission of authority. 3 、 Forestry Act To protect the forest resources and to maximize the public welfare and economic effectiveness, some of the properties are classified as forestry land and being managed by authority. Based on the Forestry Act, management authority has to restrict the area of cutting timber and to identify the area or period of restricted digging of greensward, tree roots, and grass roots, based on the condition of the forest. In addition, to maintain the current ecological environment in the forest, and to preserve the diversity of species, identification of natural preserved area is needed inside the forestland. The entrance and exit of human and vehicles are controlled based on the nature of the resources inside the preserve area. Unless obtaining the approval from the management authority, not a single activity of damaging, logging or digging soil, stones, greensward and roots is allowed. Furthermore, any unauthorized activity of collecting specimen inside the forest recreation area and natural reserve will be fined. Collecting flowers and plants in these areas, or trespassing the natural reserve will also be fined. Only the activities taken by the aborigines to sustain their living or accommodate their customs are not restricted. 4 、 Cultural Heritage Preservation Act The objectives of setting up the Cultural Heritage Preservation Act are to preserve and apply the cultural resources, to enrich the spiritual lives of citizens, and to add glory to the existing diverse cultures. The Cultural Heritage Preservation Act classifies the natural landscape and scenery as cultural assets. Vistas of Natural Culture refer to the natural areas, landforms, plants and mineral which contain the values of preservation. It can be further grouped into natural preserved area and natural monuments. Since the natural monuments include the unusual plants and mineral, it is connected to the management of biological resources. According to the Cultural Heritage Preservation Act, unless approved by the management authority, it is prohibited to collect, log, destroy the plants or bio resources classified as natural monuments or trespass into the area of natural preserve. For the purposes of academic research, or for the memorial ceremony of aboriginal custom, research institute and the aborigines can collect the natural monuments without the approval of authority. 5 、 Aboriginal Basic Act To protect the basic rights of the aborigines, and to sustain and develop the aboriginal society, the Aboriginal Basic Act was designed and enacted. The government not only admits the aborigine's rights in lands and natural resources, but also permits the non-profit behaviour such as hunting of wildlife, colleting of wild plants and fungi for the objective of complying with traditional culture, ceremony or private uses. In addition, the Aboriginal Basic Act provides the requirement of Prior Informed Consent (PIC) to require government or private individual to inform the aborigines before they proceed with land development, resource exploitation, ecological preservation, and academic research in the land where the aborigines live. They need to consult and obtain the aborigines' agreement or participation, and to share the related interests derived from this project. In the case of restricting the aborigine's right of the use of land or natural resources by law, the government,shall consult with the aborigines or the tribe and reach the agreement. When the government wish to design and establish national park, national scenic area, forestry area, ecological protection area, recreational area, or other resource management authorities, the government should obtain the agreement from the local aborigines and to build up the co-management mechanism.
Introduction to the “Public Procurement for Startups” mechanismIntroduction to the “Public Procurement for Startups” mechanism I.Backgrounds According to the EU’s statistics, government procurement budget accounted for over 14% of GDP. And, according to the media report, the total amount of government procurement in Taiwan in 2017 accounted for nearly 8%. Therefore, the government’s procurement power has gradually become a policy tool for the government to promote the development of innovative products and services. In 2017, the Executive Yuan of the R.O.C.(Taiwan)announced a government procurement policy named “Government as Good Partners with Startups (政府成為新創好夥伴)”[1] to encourage government agencies and State-owned Enterprises to procure and adopt innovative goods or services provided by startups. This policy was subsequently implemented through an action plan named “Public Procurement for Startups”(新創採購)[2] by the Small and Medium Enterprise Administration(SMEA).The action plan mainly includes two important parts:One created the procurement process for startups to enter the government contracts market through inter-entities contracts. The other accelerated the collaboration of the government agencies and startups through empirical demonstration. II.Facilitating the procurement process for startups to enter the government market In order to help startups enter the government contracts market in a more efficient way, the SMEA conducts the procurement of inter-entity supply contracts with suppliers, especially startups, for the supply of innovative goods or services. An inter-entity supply contract[3] is a special contractual framework, under which the contracting entity on behalf of two or more other contracting parties signs a contract with suppliers and formulates the specifics and price of products or services provided through the public procurement process. Through the process of calling for tenders, price competition and so on, winning tenderers will be selected and listed on the Government E-Procurement System. This framework allows those contracting entities obtain orders and acquire products or services which they need in a more efficient way so it increases government agencies’ willingness to procure and use innovative products and services. From 2018, the SMEA started to undertake the survey of innovative products and services that government agencies usually needed and conducted the procurement of inter-entity supply contracts for two rounds every year. As a result, the SMEA plays an important role to bridge the demand and supply sides for innovative products or services by means of implementing the forth-mentioned survey and procurement process. Moreover, in order to explore more innovative products and services with high quality and suitable for government agencies and public institutions, the SMEA actively networked with various stakeholders, including incubators, accelerators, startups mentoring programs sponsored by private and public sectors and so on. Initially the items to be procured were categorized into four themes which were named the Smart Innovations, the Smart Eco, the Smart Healthcare, and the Smart Security. Later, in order to show the diversity of the innovation of startups which response well to various social issues, from 2019, the SMEA introduced two new theme solicitations titled the Smart Education and the Smart Agriculture to the inter-entities contracts. Those items included the power management systems, the AI automated recognition and image warning system, the chatbot for public service, unmanned flying vehicles, aerial photography services and so on. Take the popular AI image warning system as an example, the system is used by police officers to make instant evidence searching and image recording. Other government agencies apply the innovative system to the investigation of illegal logging and school safety surveillance. Moreover, the SMEA has also offered subsidy for local governments tobuy those items provided by startups. That is the coordinated supporting measure which allows startups the equal playing field to compete with large companies. The Subsidy scheme is based on the Guideline for Subsidies on Procurement of Innovative Products and Services[3] (approved by the Executive Yuan on March 29, 2018 and revised on Feb. 20, 2021). In the Guideline, “innovative products and services” refer to the products, technologies, labor, service flows or items and services rendered with creative activities through deploying scientific or technical means and a certain degree of innovations by startups with less than five years in operation. Such innovative products and services are displayed for the inter-entity supply contractual framework administered by the SMEA for government procurement. III.Accelerating the collaboration of the government agencies and startups through empirical demonstration To assist startups to prove their concepts or services, and become more familiar with the governemnrt’s needs, the SMEA also created a mechanism called the “Solving Governmental Problems by Star-up Innovation”(政府出題˙新創解題). It plans to collect government agencies’ needs, and then solicit innovative proposals from startups. After their proposals are accepted, startups will be given a grant up to one million NT dollars to conduct empirical studies on solution with government agencies for about half a year. Take the cooperation between the “Taoyuan Long Term Care Institute for Older People and the Biotech Startup” for example, a care system with sanitary aids was introduced to provide automatic detection, cleanup and dry services for the patients’discharges, thus saving 95% of cleaning time for caregivers. In the past, caregivers usually spent 4 hours on the average in inspecting old patients, cleaning and replacing their bedsheets as their busy daily routines. Inadequate caregivers makes it difficult to maintain the care quality. If the problem was not addressed immediately, it would make the life of old patients more difficult. IV.Achievements to date Since the promotion of the products and services of the startups and the launch of the “Public Procurement for Startups” program in 2018, 68 startups, with the SMEA’s assistance, have entered the government procurement contracts market, and more than 100 government agencies have adopted the innovative resolutions. With the encouragement for them in adopting and utilizing the fruits of the startups, it has generated more than NT$150 million in cooperative business opportunities. V.Conclusions While more and more startups are obtaining business opportunities from the favorable procurement process, constant innovation remains the key to success. As such, the SMEA has regularly visited the government agencies-buyers to obtain feedbacks from startups so as to adjust and optimize the innovative products or services. The SMEA has also regularly renewed the specifics and items of the procurement list every year to keep introducing and supplying high-quality products or services to the government agencies. Reference: [1] Policy for investment environment optimization for Startups(2017),available athttps://www.ndc.gov.tw/nc_27_28382.(last visited on July 30, 2021 ) [2] https://www.spp.org.tw/spp/(last visited on July 30, 2021 ) [3] Article 93 of Government Procurement Act:I An entity may execute an inter-entity supply contract with a supplier for the supply of property or services that are commonly needed by entities. II The regulations for a procurement of an inter-entity supply contract, the matters specified in the tender documentation and contract, applicable entities, and the related matters shall be prescribed by the responsible entity. [4] https://law.moea.gov.tw/LawContent.aspx?id=GL000555(last visited on July 30, 2021)
Observing Recent Foreign Developments upon Bio-medicine、 Marketing Medical Devices、Technology Development Project and the Newest Litigation Trend Concerning the Joint Infringement of Method/Process Patents1、Chinese REACH has put into shape, how about Taiwan REACH? - A Perspective of Chinese Measures on Environmental Management of New Chemical Substances Taiwan food industry has been struck by the government agency's disclosure that certain unfaithful manufacturers have mixed toxic chemicals into the food additives for the past 30 years, and the chemicals may seriously threaten public health. This event has not only shocked the confidence of the customers to the industry, but also drew public attention on the well-management and the safe use of chemicals. In order to manage the fast advancing and widely applicable chemical substance appropriately, the laws and regulations among the international jurisprudences in recent years tend to regulate unfamiliar chemicals as “new chemical substances” and leverage registration systems to follow their use and import. REACH is one the most successful models which has been implemented by European Union since 2006. China, one of our most important business partners, has also learned from the EU experience and implemented its amended " Measures on Environmental Management of New Chemical Substances" (also known as "Chinese REACH") last year. It is not only a necessity for our industry which has invested or is running a business in China to realize how this new regulation may influence their business as differently , but also for our authority concerned to observe how can our domestic law and regulation may connect to this international trend. Therefore, except for briefing the content of Chinese REACH, this article may also review those existing law and regulations in Taiwan and observe the law making movement taken by our authority. We expect that the comparison and observation in this article may be a reference for our authorities concerned to map out a better environment for new chemical management. 2、The study on Taiwanese businessmen Join the Bid Invitation and Bidding of Science and Technology Project China government invests great funds in their Science and Technology Project management system, containing most of innovated technology. It also creates the great business opportunity for domestic industry. China government builds up a Bid Invitation and Bidding Procedure in the original Science and Technology Project Regime recent years, in order to make the regime become more open and full of transparency. It also improves Regime to become more fairness and efficiency. Taiwan industry may try to apply for those Science and Technology Project, due to this attractive opportunity, but they should understand china's legal system before they really do that. This Article will introduce the "Bid Invitation and Bidding Law of the Peoples Republic of China", and the "Provisional Regulation on Bid Invitation and Bidding of Science and Technology Project", then clarify applied relationship between the "Bid Invitation and Bidding Law of the Peoples Republic of China", and "Government Procurement Law of the Peoples Republic of China". It also analyzes "Bid Invitation and Bidding Procedure", "Administration of Contract Performance Procedure", "Inspection and Acceptance Procedure", and "Protest and Complaint Procedure, providing complete legal observation and opinion for Taiwan industry finally. Keyword Bid Invitation and Bidding Law of the Peoples Republic of China; Government Procurement Law of the Peoples Republic of China; Provisional Regulation on Bid Invitation and Bidding of Science and Technology Project; Applying for Science and Technology Project Regime; Bid Invitation and Bidding Procedure; Administration of Contract Performance Procedure; Inspection and Acceptance Procedure; Protest and Complaint Procedure. 3、Comparing the Decisions of the United States Supreme Court regarding Preempting Marketing Medical Devices and Drugs from State Tort Litigations with the Decision of a Hypothetical Case in Taiwan The investment costs of complying with pertinent laws and regulations for manufacturing, marketing, and profiting from drugs and medical devices (abbreviated as MD) are far higher than the costs necessary for securing a market permit. The usage of MD products contains the risk of harming their users or the patients, who might sue the manufacturer for damages in the court based on tort law. To help reduce the risk of such litigation, the industry should be aware of the laws governing the state tort litigations and the preemption doctrine of the federal laws of the United States. This article collected four critical decisions by the United States Supreme Court to analyze the requirements of federal preemption from the state tort litigations in these cases. The article also analyzed the issues of preemption in our law system in a hypothetical case. These issues include the competing regulatory requirements of the laws and regulations on the drugs and MDs and the Drug Injury Relief Act versus the Civil Code and the Consumer Protection Law. The article concluded: 1. The pre-market-approval of MD in the United States is exempted from the state tort litigations; 2. Brand-name-drug manufacturers must proactively update the drug label regarding severe risks evidenced by the latest findings; 3. Generic-drug manufacturers are exempted from the product liability litigations and not required to comply with the aforementioned brand-name-drug manufacturers' obligation; 4. No preemption issues are involved in these kinds of product liability litigations in our country; 5. The judge of general court is not bound by the approval of marketing of drug and MD; 6. The judge of general court is not bound by the determination and verdict of the Drug Injury Relief Act. 4、Through Computer-Aided Detection Software, Comparing by Discussing and Analyzing the Regulatory Requirements for Marketing Medical Devices in the United States and in Taiwan Computer-Aided Detection (CADe) software systematically assists medical doctors to detect suspicious diseased site(s) inside patients' bodies, and it would help patients receive proper medical treatments as soon as possible. Only few of this type of medical device (MD) have been legally marketed either in the United States of America (USA) or in Taiwan. This is a novel MD, and the rules regulating it are still under development. Thus, it is valuable to investigate and discuss its regulations. To clarify the requirements of legally marketing the MD, this article not only collects and summarizes the latest draft guidance announced by the USA, but also compares and analyzes the similarities and differences between USA and Taiwan, and further explains the logics that USA applies to clarify and qualify CADe for marketing, so that the Department of Health (DOH) in Taiwan could use them as references. Meanwhile, the article collects the related requirements by the Administrative Procedure Act and by the Freedom of Government Information Law of our nation, and makes the following suggestions on MD regulations to the DOH: creating product code in the system of categorization, providing clearer definition of classification, and actively announcing the (abbreviated) marketing route that secures legal permission for each individual product. 5、A Discussion on the Recent Cases Concerning the Joint Infringement of Method/Process Patents in the U.S. and Japan In the era of internet and mobile communication, practices of a method patent concerning innovative service might often involve several entities, and sometimes the method patent can only be infringed jointly. Joint infringement of method/process patents is an issue needed to be addressed by patent law, since it is assumed that a method patent can only be directly infringed by one entity to perform all the steps disclosed in the patent. In the U.S., CAFC has established the "control or direction" standard to address the issue, but the standard has been criticized and it is under revision now. In Japan, there is no clearly-established standard to address the issue of joint infringement, but it seems that the entity that controls and benefits from the joint infringement might be held liable. Based on its discussion about the recent development in the U.S. and Japan, this article attempts to provide some suggestions for inventors of innovative service models to use patents to protect their inventions properly: they should try to avoid describing their inventions in the way of being practiced by multi-entities, they should try to claim both method and system/apparatus inventions, and they should try to predict the potential infringement of their patents in order to address the problem of how to prove the infringement.
- Impact of Government Organizational Reform to Scientific Research Legal System and Response Thereto (1) – For Example, The Finnish Innovation Fund (“SITRA”)
- The Demand of Intellectual Property Management for Taiwanese Enterprises
- Blockchain in Intellectual Property Protection
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System
- Recent Federal Decisions and Emerging Trends in U.S. Defend Trade Secrets Act Litigation
- The effective and innovative way to use the spectrum: focus on the development of the "interleaved/white space"
- Copyright Ownership for Outputs by Artificial Intelligence
- Impact of Government Organizational Reform to Research Legal System and Response Thereto (2) – Observation of the Swiss Research Innovation System
